Our team of Computer Digital Forensics Investigators and Forensics Security Consultants are the Digital Forensics Experts you seek.
Digital Forensics Services
During a breach, it's essential to move quickly and contain the threat to minimize the impact by determining the root cause. However, overlooking evident procedures can limit your ability to help legal or governmental authorities pursue the threat actor.
Our Digital Forensics Investigators’ first step is to determine the purpose and objective of the investigation in a free consultation. We will work with you to identify where your data is located. We will document the legal chain of custody of the media and we will make a bit-by-bit copy and preserve the original. The Digital Forensics Analysis will examine and extract the data that can be viewed by the operating system, as well as data that is invisible to the operating system - including deleted data that has not been overwritten,
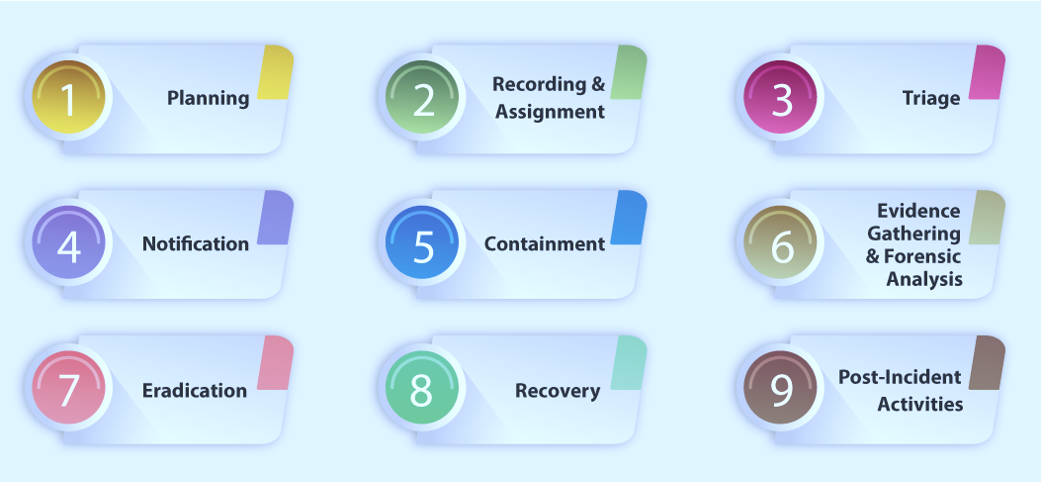
Incident Response and Forensic Lifecycle
DIGITAL FORENSICS SERVICES AND MALWARE ANALYSIS
Our IT Security team will thoroughly investigate the incident while keeping you informed of all results. Computer forensic investigations can be performed during Incident Response Handling or independently - depending on your needs. Our experts leverage elite cyber threat intelligence to investigate the breach(es), determine likely cause(s), report progress to appropriate parties as required by many regulatory compliance and security standards, and help you contain and eradicate the threat from your environment quickly as possible.
CyberSecOp digital forensics experts specialize in cyber incident response and data investigations on computers, mobile devices, servers, dark web and other systems.