CYBER SECURITY CONSULTING SERVICE AWARDS AND RECOGNITIONS
CyberSecOp's comprehensive managed security services, cyber security consulting, professional services, and data protection technology are recognized as industry-leading threat detection and response solutions by major analyst firms, key media outlets, and others.
How MSSPs Secure the Financial Sector Against Cyber Heists and Fraud
The financial sector faces relentless cyber threats in 2025, from sophisticated heists stealing millions to widespread fraud exploiting digital banking. Banks and financial institutions handle sensitive data and high-value transactions, making them prime targets for cybercriminals. Managed Security Service Providers (MSSPs) deliver tailored cybersecurity solutions to meet stringent regulatory demands and protect against evolving attacks.
Unique Cybersecurity Challenges in the Financial Sector
Regulatory Compliance Pressures
Financial institutions must adhere to rigorous standards like PCI DSS, GLBA, SOX, and FFIEC guidelines. Non-compliance risks massive fines—up to 4% of global revenue under GDPR—and reputational damage.
High-Value Transaction Vulnerabilities
Real-time payment systems, SWIFT networks, and mobile banking create opportunities for fraud, with cyber heists averaging $4.5 million per incident.
Advanced Persistent Threats (APTs)
Nation-state actors and organized crime groups launch targeted attacks using zero-days, supply chain compromises, and insider threats to infiltrate core banking systems.
Fraud at Scale
Account takeover (ATO), synthetic identity fraud, and payment redirection scams surged 35% in 2025, exploiting AI-driven automation.
How MSSPs Provide Tailored Solutions for Financial Institutions
24/7 Security Operations Centers (SOCs) with Financial Expertise
MSSPs deploy specialized SOC teams trained in financial crime patterns, monitoring transactions, logs, and endpoints continuously to detect anomalies like unusual wire transfers or login spikes.
Real-Time Transaction Monitoring
Advanced behavioral analytics flag suspicious activities, such as high-velocity small transactions or geographic mismatches, preventing fraud before settlement.
Zero Trust Architecture Implementation
MSSPs enforce strict identity verification, micro-segmentation, and least-privilege access across hybrid cloud and on-premises banking environments, limiting lateral movement during breaches.
Multi-Factor Authentication (MFA) and Biometrics
Adaptive MFA combines device trust, behavioral biometrics, and risk-based authentication to secure remote access for tellers, traders, and executives.
AI-Powered Fraud Detection and Prevention
Machine learning models analyze petabytes of transaction data in real-time, identifying synthetic identities, ATO attempts, and deepfake-driven scams with 99% accuracy.
Threat Hunting for APTs
Proactive hunts using MITRE ATT&CK frameworks uncover dormant threats in core banking systems, SWIFT gateways, and third-party vendor networks.
Comprehensive Compliance and Audit Support
MSSPs automate evidence collection for PCI DSS, SOC 2, and FFIEC audits, generating executive reports that demonstrate control effectiveness and risk posture.
Incident Response Tailored to Financial Regulations
Pre-defined playbooks ensure rapid containment while preserving chain-of-custody for regulatory notifications within mandatory timelines (e.g., 72 hours under GDPR).
Endpoint and Network Protection for Branch Operations
MSSPs secure ATMs, POS terminals, and branch networks with EDR, next-gen firewalls, and Deception Technology that lures attackers into honeypots.
Vendor and Third-Party Risk Management
Continuous monitoring of fintech partners, payment processors, and cloud providers prevents supply chain attacks that compromise 40% of financial breaches.
Proven Benefits of MSSP Partnerships for Banks
Reduced Fraud Losses: Clients report 60-80% drops in unauthorized transactions.
Faster Breach Containment: Mean time to respond (MTTR) under 30 minutes vs. industry average of 277 days.
Premium Reductions: Cyber insurance discounts of 20-30% through demonstrated security maturity.
Scalability: Handles peak volumes during trading hours or tax seasons without staffing spikes.
Conclusion
Financial institutions cannot afford downtime or data compromise in a sector where trust equals revenue. MSSPs like CyberSecOp provide the specialized expertise, technology stack, and regulatory alignment needed to secure against cyber heists, fraud rings, and APTs while enabling digital innovation.
Partner with CyberSecOp for Financial Sector Cybersecurity
Fortify your bank's defenses with CyberSecOp's MSSP solutions designed specifically for the financial industry. From transaction monitoring to compliance automation, we deliver enterprise-grade protection tailored to your risk profile.
Contact us today to schedule a financial security assessment:
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
Deepfake Fraud: How Cybercriminals Are Using AI to Impersonate Executives
Deepfake fraud has surged in 2025, with cybercriminals using AI-generated videos, audio, and voice clones to impersonate executives in scams targeting businesses. These attacks trick employees into transferring funds, revealing sensitive data, or granting unauthorized access, resulting in multimillion-dollar losses like the $25 million Arup incident in 2024.
The Rise of Deepfake Executive Impersonation
AI tools enable attackers to create hyper-realistic deepfakes from mere seconds of public audio or video, such as podcasts or webinars. Common tactics include:
Vishing (Voice Phishing): Cloned executive voices in urgent calls demanding wire transfers or confidential info, with vishing attacks up 170% in Q2 2025.
Video Deepfakes: Real-time face-swaps during video calls, fooling even security experts; 40% of IT pros reported executive deepfake targets in 2025, up from 33% in 2023.
Whaling Attacks: Highly targeted scams mimicking CEOs or CFOs via multi-channel escalation (email, calls, video), often bypassing biometrics.
BEC (Business Email Compromise): Deepfakes combined with phishing to divert vendor payments.
Deepfake files exploded from 500K in 2023 to 8M in 2025, with fraud attempts spiking 3,000%.
Business Impacts and Real-World Examples
These scams exploit trust in leadership, causing financial devastation, data breaches, and reputational harm. Attackers target finance/HR teams under end-of-quarter pressure, leading to unauthorized transactions or espionage. Executives face personal risks too, as breaches extend to home networks. Startups like imper.ai raised $28M in December 2025 to combat this boom.
How MSSPs Mitigate Deepfake Threats
Managed Security Service Providers (MSSPs) deploy layered defenses to detect and neutralize deepfakes:
AI-Powered Detection Tools: Analyze media for inconsistencies in audio-visual data, voice patterns, and liveness challenges to verify authenticity in real-time.
Behavioral Analytics and UEBA: Monitor anomalies like unusual access requests or multi-channel escalations tied to impersonation attempts.
Phishing Simulations and Training: Run realistic deepfake/vishing drills with executive clones, code-phrase systems, and verification protocols (e.g., callback policies).
Incident Response Playbooks: 90-day frameworks for risk assessment, technical controls (e.g., payment gates), and board reporting to contain scams swiftly.
Threat Intelligence Integration: Track emerging deepfake tools like Deep-Live-Cam and global IoCs for proactive blocking.
These measures reduce human error—the key deepfake vulnerability—while automating responses.
Conclusion
Deepfake executive impersonation exploits AI realism and human trust, driving massive fraud in 2025. MSSPs counter with advanced detection, training, and rapid response, turning potential crises into manageable risks.
Protect Against Deepfake Fraud with CyberSecOp
Secure your executives and teams from AI scams through CyberSecOp’s MSSP services featuring deepfake detection and proactive defenses.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
Cyber Insurance: What It Covers (and Why an MSSP is Still Necessary)
Cyber insurance provides financial protection against the aftermath of cyberattacks, covering costs like data breaches and ransomware that average $3.86 million per incident in 2025. With the global market reaching $20.56 billion this year and 62% of firms now insured (up from 49% in 2024), policies help mitigate recovery expenses—but they do not prevent attacks or reduce premiums without strong defenses.
What Cyber Insurance Typically Covers
Policies vary but generally include first-party (direct business losses) and third-party (liability to others) coverage:
Data Breaches and Incident Response: Forensic investigations, notification costs, and credit monitoring for affected individuals.
Ransomware and Extortion: Payments (where allowed), decryption tools, and recovery efforts; ransomware drives 60% of large claims.
Business Interruption: Lost revenue from downtime during recovery.
Legal and Regulatory Fines: Defense costs, settlements, and penalties for non-compliance (e.g., GDPR, HIPAA).
Reputation Management and Third-Party Claims: PR support and lawsuits from customers or partners.
Exclusions are tightening, often denying claims for outdated software, unpatched systems, or poor cybersecurity hygiene, pushing premiums up 15-20% annually.
Why Businesses Still Need MSSPs for Proactive Security
Cyber insurance is reactive—it pays after damage occurs and increasingly requires proof of robust security (e.g., MDR, EDR) for coverage or lower rates, with proactive measures cutting premiums by up to 20%. MSSPs provide essential prevention that insurance cannot:
Continuous Threat Monitoring and Detection: 24/7 SOCs identify threats early, reducing breach likelihood and claim frequency (down 50% in 2025).
Incident Response and Remediation: Rapid containment minimizes downtime and costs, preserving insurability.
Compliance and Risk Management: Automated audits and frameworks ensure policies remain valid amid stricter underwriting.
Advanced Defenses: AI-driven tools combat ransomware (33% of claims from manufacturing) before escalation.
Without MSSPs, businesses face higher premiums, claim denials, and uninsurable risks in a market projected to hit $30 billion by 2030.
Conclusion
Cyber insurance safeguards finances post-breach but demands proactive security for viability. MSSPs deliver the prevention, monitoring, and response that keep attacks at bay, ensuring coverage remains affordable and effective.
Strengthen Your Defenses with CyberSecOp
Combine cyber insurance with CyberSecOp’s MSSP services for comprehensive protection and premium savings.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
Cyber & AI Leadership Summit In-person EventIn Collaboration with Global CISO Leadership Foundation
Modern cyber risk is accelerating faster than most organizations can adapt—and 2026 will be defined by AI driven threats, expanding attack surfaces, legal uncertainty, and rising board expectations.
From agentic AI and external exposure to cyber insurance, Zero Trust, legal risk, GRC modernization, ransomware resilient architectures, and an executive CISO panel, this event delivers the insights and peer dialogue required to stay ahead of what’s coming next.
Wednesday, March 11, 2026
9:00 AM 5:00 PM
Hotel NoMa ,1 Radisson PlazaNew Rochelle, NY, 10801United States (map)
9-9:30AM EST (30min)
Welcome, Networking Breakfast & Partner Tables - Sponsored by 360Advanced
9:30 -9:45AM EST (15min)
Kickoff and Agenda
Featured Speakers: Gina Fideli, P3 Transformation Founder - HOST
Set the tone, expectations & session logistics and Introductions
9:45-10:30AM EST (45min)
Opening Keynote: “Reasonable Security in the Era of Agentic AI”
Featured Speakers: Curtis Dukes, Executive Vice President & General Manager, Center for Internet Security (CIS) & Chirag Arora, Global Ambassador, Center for Internet Security; Chair, Global CISO Leadership Foundation.
This keynote will examine what “reasonable security” means as enterprises adopt agentic AI systems capable of autonomous decision-making. The session will explore governance expectations, evolving definitions of due care, and practical frameworks organizations can adopt today.
10:30-11:15AM EST (45min)
Roadmap to Closing Your Organization’s External Security Gaps: Managing External Exposure, Brand Risk, and Dark Web Threats in a Rapidly Expanding Attack Surface
Presenter: Chirag Arora, Global Security Leader
Session Overview
As organizations rapidly expand their digital footprint across cloud, SaaS, AI integrations, and third-party ecosystems, external exposure has become the fastest-growing source of cyber risk. Traditional internal security controls alone are no longer sufficient to detect, prioritize, or prevent real-world breaches.
This session provides a practical, board-level roadmap for identifying and closing security gaps across external attack surface, brand abuse, and dark web intelligence, using real-world threat patterns and exposure data.
11:15-12:00PM EST (45min)
Security vs. Compliance: Why “Checking the Box” Keeps Failing CISOs: A Think Tank on Bridging Real Risk Reduction and Regulatory Expectations
Format: Think Tank Discussion
Facilitator: Oscar Jones, CISO, CyberSecOp
Session Framing
Security and compliance are often treated as interchangeable—but in practice, they frequently work against each other. Organizations pass audits yet still get breached. CISOs invest heavily in frameworks, assessments, and controls, while attackers continue to exploit gaps that compliance programs never surface.
This think tank brings security leaders together to challenge conventional thinking, examine real-world failures, and explore how CISOs can move beyond checkbox compliance toward measurable risk reduction—without breaking regulatory alignment.
12-12:15PM (15min)
Properly Sizing Cyber Insurance
Speaker: Imani Barnes, Associate Director, RiskStrategies
Session Overview
Cybersecurity can lower your risk, but it can’t protect you from every weak link in your digital ecosystem. With cyber incidents and business interruption ranked as the top global risks, organizations must prepare for the ripple effects of third‑party failures. That’s why cyber insurance, especially contingent business interruption coverage, has become an essential safety net for the threats you can’t control.
12:15-12:45PM Sponsored by RiskStrategies
Lunch, Networking Break
12:45-1:30PM (45min)
Operationalizing Zero Trust at the Browser Layer: Real-World Use Cases Enabled
Speaker: MacKenzie Miller, CAM of Island.io
Session Overview
As work increasingly happens inside the browser—across SaaS, cloud consoles, AI tools, and legacy web apps—the browser has become the new control plane for enterprise security, data protection, and compliance.
This session shows how Island’s Enterprise Browser Console modules enable organizations to secure access, prevent data loss, and reduce attack surface without agents, VPNs, or virtual desktops—while preserving user experience.
1:30-2:15PM EST (45min)
Legal Deep Dive: “AI Agents, Liability & the Courts: Lessons from Perplexity v. Amazon”
Speaker: Antony Haynes, Professor of Law, Albany Law School; Group Head, Cybersecurity, Data Privacy & AI Practice, Dorf Nelson & Zauderer LLP
A forward-looking analysis of the emerging legal landscape for both developers of agentic systems and organizations deploying agents as users. Using Perplexity v. Amazon as the anchor case, this session will cover IP liability, contractual risk allocation, tort exposure, and what corporate counsel must anticipate as AI autonomy increases.
2:15-2:45 EST (30min)
Operationalizing Cyber Resilience: Turning GRC from Compliance Burden into Business Capability: How Modern GRC Enables Measurable Resilience Across Security, Risk, and Operations
Speakers: Shareth Ben, VP of Sales & Strategy, Apptega & Tom Guadagno, CISO of CyberSecOp
Session Overview
Most organizations invest heavily in Governance, Risk, and Compliance (GRC), yet struggle to translate frameworks, assessments, and policies into day-to-day operational resilience. GRC is often perceived as documentation-heavy and reactive—disconnected from how security teams actually manage risk.
This session explores how modern GRC programs can be operationalized to drive real resilience by aligning security operations, risk management, and compliance into a single, actionable system of record.
2:45-3:15PM EST (30min)
How Unified Audits Reduce Cost, Fatigue and Improve Security Program Maturity
Speakers: Jim Brennan, Sr. Compliance Executive
Session Overview
An Audit Once, Report Many methodology is designed to streamline the entire experience by consolidating the overlapping requirements across frameworks and conducting a single, comprehensive audit that supports all the needed reports. We gather evidence once, validate controls once, and then map the results into each relevant framework for delivery. The result? A more efficient, predictable, and less disruptive audit experience.
3:15-3:50 EST (35min)
Ransomware-Proof by Design: Building Resilient, Recoverable, and Trustworthy Data Backups: How Modern Enterprises Ensure Recovery When Prevention Fails
Presenter: Nutanix (Speaker TBD – Field CTO / Distinguished Technologist / Security Architect)
Session Overview
Ransomware is no longer just an encryption event—it is a data integrity and recovery crisis. Attackers increasingly target backups first, corrupt recovery points, and exploit operational complexity to delay restoration.
This session explores how organizations can design robust, ransomware-resilient backup and recovery architectures that assume compromise, preserve trust in data, and enable rapid, confident recovery—without adding operational overhead.
3:50-4:30PM EST (40min)
CISO Executive Panel: “AI Exposure: The Next-Generation Challenge for Cyber Leaders”
Panelists: Oscar Jones, Mike Schimenti & Tom Guadagno, Cybersecurity CISOs, Chirag Arora, Chair, Global CISO Leadership Foundation & Additional New York–based CISO (TBD)
A practical and strategic discussion on how AI-driven exposures—LLM integration, agentic automation, API misuse, data governance gaps, and digital supply chain risks—are reshaping the CISO agenda for 2025–2026. This panel will highlight real-world scenarios, defense strategies, and what cyber leaders need to prioritize now.
4:30-5PM EST
Raffle + Closing Remarks
Featured Speakers: Gina Fidely/HOST & Vinny LaRocca/CEO
5 -6PM EST Sponsored by Island.io
Happy Hour + Open Networking
MSSP vs. MDR: Understanding the Differences and Which One Your Business Needs
In 2025, cybersecurity solutions have become more specialized, and businesses often face the choice between engaging a Managed Security Service Provider (MSSP) or a Managed Detection and Response (MDR) service.
In 2025, cybersecurity solutions have become more specialized, and businesses often face the choice between engaging a Managed Security Service Provider (MSSP) or a Managed Detection and Response (MDR) service. Both play vital roles in enhancing cybersecurity, but they serve distinct purposes and offer different capabilities. Understanding these differences will help you decide which solution fits your organization's security needs.
What is an MSSP?
A Managed Security Service Provider (MSSP) offers a broad range of outsourced security management services. Their core focus is on prevention, management, and monitoring of security infrastructure, including firewalls, antivirus solutions, vulnerability assessments, patch management, compliance management, and alert monitoring. MSSPs primarily act as an extension of an organization's internal security team, providing 24/7 monitoring and alerting based on predefined thresholds.
Key Characteristics of MSSPs:
Scope: Broad security service coverage including device management, compliance, and basic incident alerting.
Approach: Emphasis on prevention through controls, configurations, and monitoring.
Response: Typically alert-based — MSSPs notify the organization about security events; internal teams often handle in-depth investigations and responses.
Expertise Level: General cybersecurity skills across various domains.
Cost: Generally more cost-effective than MDR, especially for organizations requiring broad security coverage.
Integration: May require complex setups integrating with existing client infrastructure.
What is MDR?
Managed Detection and Response (MDR) is a specialized service focusing specifically on continuous threat detection, proactive hunting, and rapid incident response. MDR providers assume that breaches can occur, so their priority lies in swiftly identifying and neutralizing active threats to minimize damage.
Key Characteristics of MDR:
Scope: Focused on detecting sophisticated threats, incident investigation, and remediation.
Approach: Proactive and real-time threat detection combined with immediate response.
Response: Hands-on involvement, including investigation, containment, and mitigation by the MDR team.
Expertise Level: Highly specialized analysts skilled in deep detection, threat hunting, and forensics.
Cost: Typically higher than MSSPs, reflecting the depth of response and expertise.
Integration: Requires tight integration with endpoint, network, and security tools for optimal detection and response.
Comparing MSSP and MDR Side by Side
| Aspect | MSSP | MDR |
|---|---|---|
| Primary Focus | Security infrastructure management, monitoring, and alerting | Real-time threat detection, hunting, and incident response |
| Security Approach | Preventive and reactive | Proactive and reactive |
| Alert & Response | Alert-based, with response often by client | Direct response and containment by provider |
| Expertise Level | Broad cybersecurity knowledge | Specialized threat detection and incident handling |
| Service Scope | Broad security services including compliance | Focused on sophisticated attacks and rapid response |
| Cost | More affordable for broad coverage | Higher cost due to depth and immediacy of services |
| Ideal For | Organizations needing comprehensive security coverage and compliance assistance | Organizations facing advanced persistent threats needing rapid, expert response |
Which One Does Your Business Need?
Choose an MSSP if you need a broad, ongoing security management partner to handle your infrastructure, compliance, and general alert monitoring.
Choose MDR if you require specialized, proactive threat detection and a rapid incident response team that actively investigates and neutralizes ongoing attacks.
Many organizations benefit from a hybrid approach, where MSSPs provide general security support and MDR services augment detection and response capabilities.
Conclusion
While MSSPs focus on managing and monitoring your overall security posture, MDR services dive deeper to detect and respond to sophisticated, active threats. Both are integral to a comprehensive cybersecurity strategy, and selecting the appropriate service depends on your organization's risk profile, budget, and security maturity.
CyberSecOp offers both MSSP and MDR services, delivering tailored cybersecurity solutions to meet your unique business needs.
Secure Your Business with CyberSecOp
Find out which managed security solution is right for you with CyberSecOp’s expert guidance.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
How MSSPs Use Threat Hunting to Stop Cybercriminals Before They Strike
In 2025, cyber threats continue to grow in complexity, with adversaries constantly evolving tactics to evade detection.
In 2025, cyber threats continue to grow in complexity, with adversaries constantly evolving tactics to evade detection. Managed Security Service Providers (MSSPs) adopt threat hunting as a proactive security measure to identify and eliminate hidden threats before they cause damage. Unlike reactive approaches that wait for alerts, threat hunting involves actively searching for signs of compromise in network and endpoint data to uncover stealthy attackers.
Proactive Security Measures in MSSP Threat Hunting
1. Data Aggregation and Preparation
MSSPs collect and normalize diverse security data including logs, network traffic, endpoint telemetry, and threat intelligence from various sources. This consolidated dataset forms the foundation for effective threat hunting.
2. Structured and Hypothesis-Driven Hunting
Analysts use structured methodologies such as the MITRE ATT&CK framework to explore specific attacker tactics, techniques, and procedures (TTPs) relevant to client environments. Hypotheses based on recent threat intelligence or behavioral anomalies guide targeted searches to uncover hidden malicious activities.
3. AI and Machine Learning Analytics
Advanced MSSPs employ AI/ML to sift through vast datasets, identify anomalies, and correlate seemingly unrelated events that human analysts might miss. AI enhances pattern recognition for detecting novel attack vectors, reducing false positives and focusing on genuine threats.
4. Threat Intelligence Integration
Real-time threat intelligence feeds inform hunters about emerging Indicators of Compromise (IoCs) and new adversary profiles. This intel enriches hunts, enabling early detection of known and unknown threats.
5. Flexible Hunting Approaches
Combining automated exploratory scans with focused, event-driven hunts allows MSSPs to benchmark normal behavior, identify deviations, and adapt dynamically to evolving attack methods.
6. Rapid Investigation and Incident Response
Once suspicious activity is discovered, MSSPs leverage automated workflows and Security Orchestration, Automation, and Response (SOAR) tools to quickly contain threats, minimize dwell times, and reduce impact.
The Business Benefits of MSSP Threat Hunting
Early Detection: Catch attackers before they escalate attacks or exfiltrate data.
Reduced Damage: Minimize operational disruption, data loss, and financial impact.
Improved Security Posture: Identify gaps and improve defenses proactively.
Regulatory Compliance: Demonstrate proactive risk management for auditors and regulators.
Operational Efficiency: Leverage AI and automation to maximize security team productivity.
Conclusion
Threat hunting is a game-changer in cybersecurity, shifting the paradigm from waiting to respond toward actively seeking threats before damage occurs. MSSPs, equipped with advanced analytics, threat intelligence, and skilled analysts, provide organizations with this crucial proactive defense layer, significantly reducing risk and enhancing cyber resilience.
Protect Your Business with CyberSecOp’s Threat Hunting Expertise
Stay ahead of cybercriminals with CyberSecOp’s managed threat hunting services that find and stop threats before they strike.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
AI-Generated Cyber Threats: How Hackers Use AI and How MSSPs Counter It
In 2025, cybercriminals are increasingly harnessing the power of artificial intelligence (AI) to elevate their attack capabilities, creating a new breed of AI-generated cyber threats.
In 2025, cybercriminals are increasingly harnessing the power of artificial intelligence (AI) to elevate their attack capabilities, creating a new breed of AI-generated cyber threats. These AI-enhanced attacks are more sophisticated, automated, and harder to detect, posing significant risks to organizations worldwide. Managed Security Service Providers (MSSPs) leverage advanced AI-driven defenses to counter these evolving threats actively. This blog explores how hackers use AI for cyberattacks and how MSSPs employ AI to protect businesses.
How Hackers Use AI in Cyberattacks
AI-Powered Phishing and Social Engineering
Cybercriminals use AI-generated content to craft highly personalized and convincing phishing emails at scale. These messages often mimic writing styles and reference personal data, making them more difficult for users to identify as fraudulent. AI chatbots like FraudGPT are used to automate scams, increasing both reach and effectiveness.
AI-Driven Malware and Ransomware
AI enables malware to adapt in real-time, learning from the target environment to evade traditional endpoint detection and response (EDR) systems. For instance, ransomware strains like BlackMatter use AI to identify and encrypt the most valuable data while avoiding artifacts that trigger detection tools.
Deepfake Technology for Impersonation Attacks
Attackers deploy AI-generated audio and video deepfakes to impersonate executives, customers, or trusted parties, tricking employees into unauthorized transactions or divulging confidential information. The realism of these forgeries significantly complicates verification processes.
Automation of Attack Tools
Malicious AI models available on dark web forums provide “cybercrime as a service” by automating the generation of malicious code, phishing websites, and social engineering campaigns. This lowers the technical barrier for committing sophisticated cybercrime.
AI-Powered Reconnaissance
AI algorithms analyze vast data sets — including social media and network behavior — to identify vulnerabilities, map user behaviors, and pinpoint key targets for attacks, increasing the precision and success rate of campaigns.
How MSSPs Use AI to Combat AI-Generated Threats
1. AI-Enhanced Threat Detection
MSSPs deploy AI-powered Security Information and Event Management (SIEM) and User and Entity Behavior Analytics (UEBA) tools to identify anomalies and suspicious patterns indicative of AI-driven attacks, often before damage occurs.
2. Automated Incident Response and Hunting
Using AI-powered Security Orchestration, Automation, and Response (SOAR) platforms, MSSPs automate routine investigation and remediation tasks, accelerating response times and minimizing human error.
3. AI-Driven Phishing Detection
MSSPs utilize AI tools to scan inbound emails for AI-crafted phishing content, analyzing context, language nuances, and user history to block malicious messages effectively.
4. Deepfake Detection and Verification
Advanced AI models help MSSPs detect deepfake media by analyzing inconsistencies in audio-visual data, ensuring communications authenticity and preventing impersonation fraud.
5. Continuous Learning and Adaptation
MSSP AI tools continuously learn from new threat data, improving detection models in near real-time to keep pace with rapidly evolving AI-generated attack techniques.
Conclusion
The rise of AI-generated cyber threats presents unprecedented challenges for cybersecurity defense. Cybercriminals’ use of AI to automate, personalize, and evade detection requires equally sophisticated countermeasures. MSSPs, equipped with cutting-edge AI-enhanced tools and expert analysts, provide the proactive and adaptive defenses necessary to protect businesses from these next-generation threats.
Secure Your Business Against AI-Driven Cyberattacks with CyberSecOp
Partner with CyberSecOp to leverage AI-powered security technologies and expert managed services designed to detect and neutralize advanced AI-generated cyber threats.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
What the AWS Outage Exposed About Continuity, Dependency, and Real Resilience
The AWS outage in the US-East-1 region last week didn’t just disrupt services, it revealed how dependent most organizations have become on cloud providers without having continuity plans outside of them.
The recent AWS outage in the US-East-1 region wasn’t just another cloud hiccup. It was a leadership test for IT organizations across every industry, private sector, government, healthcare, finance. Some businesses stayed online. Most waited to recover. And everyone was reminded of an uncomfortable reality:
We’ve built mission-critical operations on cloud infrastructure, but we haven’t built a way to operate when it fails.
This wasn’t an attack. It wasn’t ransomware or a foreign adversary. It was an internal DNS automation failure at AWS. But the business impact was the same. Systems down, transactions halted, customers locked out, revenue on hold.
What Actually Happened
On October 20, 2025, around 3 a.m. ET, AWS experienced a failure inside its DNS automation and monitoring systems. A change removed critical DNS records for DynamoDB service endpoints, and automated recovery didn’t fix it. Applications could no longer resolve service addresses, which caused cascading failures.
By 6:01 p.m. ET, AWS declared services recovered. But the damage was already done.
Who Was Affected and How Bad Was It?
This wasn’t a small or regional outage.
According to the Guardian and Reuters, thousands of companies were affected globally. Some sources estimate well over 2,000 directly impacted providers and platforms.
Millions of end users reported failures, with more than 4 million outage reports recorded at peak.
Major platforms were affected, including Venmo, Ring, airlines, healthcare portals, banks, authentication platforms, retail sites, smart home platforms, and gaming services like Fortnite and Roblox.
Even government agencies and enterprises with segmentation, zoning, or isolated VPCs experienced interruptions, because the failure was at the provider layer, not inside customer environments.
How Much Did It Cost Businesses?
No one has a final number, but we do know this:
CyberCube estimates insured financial losses between $38 million and $581 million from this one event.
Broader economic impact, including lost revenue, productivity, and supply chain disruption, is expected to land in the hundreds of millions to billions.
Industry benchmarking tells us many enterprises lose between $300,000 and $5 million per hour of downtime. Some exceed $16,000 per minute.
A mid-size ecommerce business processing $100,000 a day in sales could have lost around $60,000 during the outage window, not including customer churn or recovery cost.
Multiply that across thousands of businesses over a 12 to 15-hour disruption, and the numbers add up quickly.
Why Some Organizations Stayed Online and Most Didn’t
This outage revealed a clear split.
| Organization Type | Outcome |
|---|---|
| Businesses with tested failover to Google Cloud, Azure, on-prem systems, or active-active infrastructure | Continued operating or saw minimal disruption |
| Organizations fully dependent on AWS US-East-1, often because of SaaS platforms, APIs, or identity providers | Operations paused until AWS recovered |
| Enterprises and government agencies with zoning, segmentation, or VPC separation | Still affected, because control plane and DNS failures sit above those protections |
| Organizations relying on Azure as a fallback | Were reminded Azure suffered a similar outage earlier in the year |
Azure Had the Same Problem with a Different Cause
Earlier in 2023, Azure experienced a major global disruption. A surge in network traffic and DDoS attempts caused Azure Portal and core services to become unavailable. Management functions, authentication, and critical services stalled.
Azure did not publish how many businesses were affected. AWS provided more detail in this recent event. Different clouds, different trigger points, same result. Operations stopped, IT teams scrambled, and executives wanted answers.
This isn’t about which cloud is safer. It’s about whether your business can keep operating when any cloud fails.
The Real Issue: Over-Dependency Without a Backup Plan
Three big problems were exposed.
Most organizations don’t have a way to function without their primary cloud provider. They have redundancy inside AWS or Azure, but nothing outside.
We’ve mistaken segmentation for resilience. Zoning, VPCs, and multi-AZ architectures are valuable, but they don’t protect against failures in DNS, identity, or control plane systems at the provider.
Business continuity hasn’t evolved at the same pace as cloud adoption. We moved applications, identity, and data to the cloud, but we never built an exit ramp for when the cloud is the problem.
What CIOs, CISOs, and IT Directors Should Be Doing Now
1. Map All Dependencies
Not just your servers. Look at identity, authentication, DNS, APIs, SaaS platforms, payments, analytics, HR systems, payroll tools. If it stops working when AWS or Azure is down, it’s a dependency you need to know about.
2. Build Continuity Outside the Cloud Provider
That could mean a secondary provider like Google Cloud or Azure, on-prem hardware, or private infrastructure for core workloads. It could include secondary DNS, offline authentication modes, or replicated data stores that aren’t tied to a single vendor.
3. Test What Happens During Failure
Run real-tabletop exercises. If AWS goes down at 10 a.m., what do you do in the first hour? Can you authenticate employees? Take payments? Access critical data? Communicate with customers and leadership?
4. Explain This Clearly to Executives
Don’t sell panic. Sell transparency and readiness.
Cloud is still the right strategy, but it isn’t immune to failure. Our goal isn’t to move away from AWS or Azure. It’s to make sure we can keep working when they don’t.
This isn’t only an IT problem. It’s business continuity.
Final Thought
Cloud is still the best place to build, scale, and secure modern systems. But uptime isn’t guaranteed. The AWS outage wasn’t a random glitch. It proved that cloud dependency without continuity is a business risk.
Some organizations stayed online. Others waited in the dark. The difference wasn’t budget or size. It was planning.
The new measure of IT leadership isn’t how well things run on a good day. It’s how well they run when the cloud isn’t there.
Zero-Day Attacks and Why Every Business Needs MSSP Protection
In 2025, zero-day attacks remain one of the most formidable cyberthreats organizations face. A zero-day attack exploits a software, hardware, or firmware vulnerability unknown to the vendor and for which no patch or fix is available.
In 2025, zero-day attacks remain one of the most formidable cyberthreats organizations face. A zero-day attack exploits a software, hardware, or firmware vulnerability unknown to the vendor and for which no patch or fix is available. Attackers leverage these undisclosed vulnerabilities before security teams have any opportunity to prepare or defend against them, making zero-day exploits highly effective and dangerous.
What are Zero-Day Attacks?
Zero-day vulnerability: A flaw or weakness in software or hardware that is unknown to vendors and without a current fix.
Zero-day exploit: The attack method malicious actors use to take advantage of the vulnerability.
Zero-day attack: When attackers successfully exploit the zero-day vulnerability to gain unauthorized access, steal data, or cause damage.
These attacks are particularly severe because they provide no warning or defense window, often giving attackers the ability to move freely inside a network and cause serious harm, from data theft to disruption of critical systems.
Why Zero-Day Attacks Are So Dangerous
Unknown and Unpatched Vulnerabilities: No immediate fix or signature exists to detect or prevent the attack.
Targeted and Sophisticated: Attackers can design exploits that evade traditional security tools.
Potential for Widespread Damage: The window between vulnerability discovery and patch release is exploited aggressively.
High Impact: Can lead to data breaches, ransomware infections, intellectual property theft, and long-term damage to business reputation.
How MSSPs Proactively Defend Against Zero-Day Attacks
1. Behavioral Analytics and Anomaly Detection
MSSPs use advanced User and Entity Behavior Analytics (UEBA) and machine learning to detect abnormal patterns in user activities and endpoint behaviors indicative of zero-day exploitation attempts.
2. Endpoint Detection and Response (EDR)
Modern EDR tools provide real-time monitoring, threat hunting, and automated containment capabilities that can identify and isolate suspicious processes or lateral movement behaviors arising from zero-day attacks.
3. Threat Intelligence Integration
MSSPs leverage global, real-time threat intelligence feeds to identify emerging zero-day activity, Indicators of Compromise (IoCs), and updated threat actor tactics to quickly respond and adapt defenses.
4. Security Orchestration, Automation, and Response (SOAR)
Automated workflows allow MSSPs to respond rapidly to detected threats, containing zero-day intrusions and minimizing damage while analysts investigate.
5. Network Segmentation and Zero Trust Architecture
MSSPs implement robust network segmentation and zero trust models to limit attackers' lateral movement, reducing the impact of zero-day breaches.
6. Continuous Patch and Vulnerability Management
Although zero-days are unknown vulnerabilities, MSSPs ensure that all known patches and security configurations are up to date, closing other attack avenues that zero-day exploits may try to use.
Conclusion
Zero-day attacks exploit unknown vulnerabilities, offering attackers a significant advantage. Traditional security solutions reliant on known threat signatures are insufficient against such stealthy and sophisticated attacks. MSSPs bring the technology, expertise, and proactive strategies necessary to detect, contain, and mitigate zero-day threats effectively.
Partnering with an MSSP like CyberSecOp ensures a resilient defense posture, employing cutting-edge behavioral analytics, threat intelligence, automated response, and comprehensive endpoint protection to safeguard your business from emerging threats—even before patches exist.
Protect Your Business from Zero-Day Attacks with CyberSecOp
Stay ahead of zero-day threats with CyberSecOp’s expert managed security services designed to detect and respond to advanced cyberattacks in real time.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
The Evolution of Insider Threats: How MSSPs Detect and Prevent Employee-Based Attacks
Insider threats have emerged as one of the most costly and complex cybersecurity risks in 2025. According to recent industry research, insider incidents cost businesses an average of $17.4 million annually, with credential theft accounting for the highest per-incident expense—nearly $780,000.
Insider threats have emerged as one of the most costly and complex cybersecurity risks in 2025. According to recent industry research, insider incidents cost businesses an average of $17.4 million annually, with credential theft accounting for the highest per-incident expense—nearly $780,000. As organizations grapple with hybrid work models, sprawling cloud environments, and an influx of SaaS tools, the risk from insiders—whether malicious or negligent—is becoming increasingly significant.
Why Insider Threats Are Growing
Expanded IT Complexity: The dissolution of traditional network perimeters, combined with hybrid work, makes monitoring insider activities more challenging.
Human Element: Insider threats often arise from misconduct, negligence, or stolen credentials. Studies show insiders contribute to over 45% of data breaches.
AI-Driven Sophistication: Adversaries are also weaponizing AI to scale and refine insider attacks.
Negligent and Malicious Insiders: Both types cause significant damage, from accidental data leaks to deliberate sabotage or theft.
How MSSPs Use Behavioral Analytics to Detect Suspicious Activities
1. Continuous User and Entity Behavior Monitoring
MSSPs deploy advanced User and Entity Behavior Analytics (UEBA) tools to monitor normal user activity baselines and detect anomalies such as unusual login times, data access patterns, or privilege escalations.
2. Real-Time Anomaly Detection and Alerting
By applying machine learning algorithms, MSSPs identify deviations from typical behavior in real time, triggering immediate alerts for potential insider incidents.
3. Risk Scoring and Prioritization
Risk scores based on behavioral factors, combined with access context (location, device, role), allow MSSPs to prioritize incidents, reducing alert fatigue and focusing attention on high-risk activities.
4. Integration with Human Resources and Security Systems
MSSPs correlate behavioral analytics with HR data (such as recent terminations or role changes) to enhance detection accuracy and response strategies.
5. Automated and Guided Incident Response
Once suspicious behavior is detected, MSSPs automate containment actions—such as session termination, account suspension, or access revocation—while providing security teams with detailed forensic evidence to investigate.
6. Continuous Improvement Through AI
Artificial intelligence models refine detection capabilities by learning from new data, adjusting thresholds, and reducing false positives, balancing security with operational continuity.
The Business Value of MSSP-Driven Insider Threat Programs
Reduced Incident Costs: Rapid detection and response reduce breach duration and financial impact.
Improved Regulatory Compliance: Demonstrates proactive insider risk management for audits and legal requirements.
Stronger Security Posture: Safeguards intellectual property, customer data, and operational continuity.
Employee Trust and Culture: Detection paired with training reinforces positive security behaviors.
Conclusion
Insider threats present an evolving and significant challenge, fueled by technology complexity, human factors, and AI-enhanced adversaries. MSSPs leverage behavioral analytics and AI-driven detection to provide comprehensive insider threat management, enabling organizations to detect, respond to, and prevent malicious or negligent insider activities effectively.
Protect Your Organization from Insider Threats with CyberSecOp
Gain peace of mind with CyberSecOp’s expert insider threat detection and prevention services powered by behavioral analytics and AI.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
Cybersecurity for Remote Work: Why VPNs and Firewalls Aren’t Enough Anymore
The dramatic shift to remote work has redefined the modern workforce landscape. While Virtual Private Networks (VPNs) and firewalls have traditionally been the cornerstone of securing remote access, the cybersecurity challenges of 2025 demand far more comprehensive strategies.
The dramatic shift to remote work has redefined the modern workforce landscape. While Virtual Private Networks (VPNs) and firewalls have traditionally been the cornerstone of securing remote access, the cybersecurity challenges of 2025 demand far more comprehensive strategies. With employees connecting from diverse locations on varying devices and networks, organizations face an expanded attack surface. Managed Security Service Providers (MSSPs) offer complete, adaptive security solutions that go beyond traditional tools to effectively secure remote workforces.
Evolving Cybersecurity Challenges of Remote Work
Increased Attack Surface
Remote work introduces multiple points of vulnerability. Employees access corporate resources from personal devices, unsecured home networks, and public Wi-Fi hotspots, creating numerous entry points for cyberattacks.
Sophisticated Cyber Threats
Cybercriminals exploit remote work environments with advanced phishing, social engineering, ransomware, and malware attacks. Attackers capitalize on distractions, lower vigilance, and inconsistent security configurations prevalent in remote settings.
Inadequate Device and Network Security
Personal devices often lack enterprise-grade antivirus and endpoint protection. Home and public networks may have weak passwords, outdated routers, and no encryption, making data interception and unauthorized access easier.
Lack of Centralized Visibility
Traditional VPNs and firewalls mostly secure network entry points but provide limited visibility into endpoint activities, user behavior, or cloud application use, hindering proactive threat detection.
Compliance Complexity
Remote work spanning multiple jurisdictions complicates regulatory compliance and data privacy enforcement, necessitating advanced monitoring and policy enforcement tools.
Why VPNs and Firewalls Alone Are No Longer Enough
VPNs Secure Transport, Not the Endpoint: VPNs encrypt communications but cannot secure the devices—often personal and minimally protected—used to access corporate resources.
Firewalls Control Traffic but Lack Context: Firewalls filter network traffic but cannot detect compromised endpoints or insider threats without endpoint visibility.
Modern Threats Bypass Traditional Defenses: Sophisticated attackers use social engineering and zero-day exploits that can circumvent VPN and firewall protections.
Limited Incident Response Capabilities: Without integrated security monitoring and automated response, attacks can go undetected for extended periods, increasing damage.
How MSSPs Provide Complete Security Solutions for Remote Workforces
1. Advanced Endpoint Detection and Response (EDR)
MSSPs deploy EDR solutions across remote devices to continuously monitor, detect, and respond to threats in real time, safeguarding endpoints beyond network perimeters.
2. Zero Trust Security Model
MSSPs implement Zero Trust frameworks verifying every access request regardless of location or device, enforcing least-privilege access and multifactor authentication (MFA) to reduce risk.
3. Cloud Access Security Broker (CASB) Integration
With increasing SaaS adoption, MSSPs use CASBs to secure cloud apps, monitor user activity, prevent data leakage, and enforce compliance policies remotely.
4. Security Information and Event Management (SIEM) & Automation
MSSPs aggregate security logs from endpoints, networks, and cloud environments using next-gen SIEM platforms integrated with Security Orchestration, Automation, and Response (SOAR) technologies for expedited threat hunting and remediation.
5. User Awareness and Phishing Simulation
Recognizing the human risk factor, MSSPs conduct regular employee training and simulated phishing campaigns to build a security-conscious culture and reduce successful attacks.
6. Network Security Enhancements
MSSPs extend firewall policies with secure web gateways, intrusion prevention, DNS filtering, and VPN enhancements optimized for remote access.
Conclusion
The remote work revolution has fundamentally challenged conventional cybersecurity approaches. VPNs and firewalls provide critical but insufficient layers of defense. Organizations must adopt a holistic security strategy—powered by MSSPs—that includes endpoint protection, identity verification, cloud security, continuous monitoring, automation, and user education.
Partnering with a skilled MSSP like CyberSecOp ensures your remote workforce remains productive, compliant, and secure in the face of today's dynamic threat landscape.
Secure Your Remote Workforce with CyberSecOp’s Managed Security Services
Enhance your remote work cybersecurity beyond VPNs and firewalls with CyberSecOp’s comprehensive MSSP solutions.
Contact Customer Service: 1 866-973-2677
Sales Inquiries: Sales@CyberSecOp.com
Endpoint Detection and Response (EDR) vs. Antivirus: Why MSSPs Rely on Advanced Security Tools
In the evolving cybersecurity landscape of 2025, Endpoint Detection and Response (EDR) solutions have emerged as a critical advancement over traditional antivirus (AV) software. Managed Security Service Providers (MSSPs) increasingly rely on EDR to provide superior endpoint protection for their clients, recognizing its ability to detect, analyze, and respond to modern, sophisticated threats with greater speed and accuracy. This article compares traditional antivirus with EDR capabilities and explains why MSSPs prefer EDR for protecting enterprise and SMB endpoints.
Why Traditional Antivirus Falls Short Today
Traditional antivirus software primarily relies on signature databases to identify threats and responds by quarantining or deleting malicious files. While effective against known malware like viruses, worms, and trojans, AV struggles with:
Zero-day and unknown threats
Fileless malware and advanced persistent threats (APTs)
Sophisticated evasion techniques that alter malware signatures on-the-fly
Limited visibility into endpoint activities beyond file scanning
As cyber attackers increasingly use polymorphic malware and attack techniques that bypass signature-based detection, traditional antivirus-based defenses fail to provide comprehensive endpoint security.
How EDR Enhances Endpoint Security
EDR tools provide continuous, behavior-based monitoring and analysis of endpoints. They use AI and machine learning to identify suspicious patterns and anomalous behaviors even when a threat has no known signature. Key benefits of EDR include:
Real-time threat detection: Continuous monitoring enables faster identification of suspicious activities like lateral movement, unauthorized privilege escalation, and unusual process execution.
Automated response: EDR platforms can automatically contain threats—isolating infected devices, terminating malicious processes, and blocking network activity—to minimize damage before human intervention is required.
Comprehensive forensics: Detailed logging and analysis capabilities allow security teams to investigate attack vectors, understand breach scope, and improve future defenses.
Improved alert prioritization: AI-driven triage reduces false positives and helps analysts focus on the most critical threats.
Adaptation to modern environments: EDR solutions can monitor endpoints across hybrid networks, cloud services, and remote work environments.
Why MSSPs Choose EDR for Endpoint Protection
Managed Security Service Providers leverage EDR platforms extensively to deliver enterprise-grade security capabilities to clients of all sizes, offering advantages such as:
Enhanced detection across evolving attack surfaces: MSSPs can secure endpoints against advanced and unknown threats that traditional AV cannot detect.
Faster incident response and remediation: Automated real-time responses reduce the window of opportunity for attackers.
Centralized, scalable monitoring: MSSPs use EDR to monitor thousands of endpoints efficiently across disparate client environments.
Rich threat intelligence and visibility: The detailed insights from EDR tools strengthen the MSSP’s ability to hunt threats proactively.
Cost-effective security: MSSPs optimize security operations by combining automated detection and response, reducing manual workloads and operational costs.
Conclusion
While traditional antivirus software remains a useful layer of defense, its limitations make it insufficient alone in today’s complex threat landscape. Endpoint Detection and Response (EDR) solutions provide continuous, intelligent monitoring and automated response capabilities critical to defending against sophisticated cyberattacks.
For MSSPs, EDR represents a cornerstone technology enabling comprehensive, scalable, and proactive endpoint protection. MSSPs like CyberSecOp utilize next-generation EDR platforms to deliver superior security outcomes to their clients, helping them stay secure and resilient.
Strengthen Your Endpoint Security with CyberSecOp
Looking for expert MSSP services that leverage advanced EDR technology to protect your business endpoints?
Contact CyberSecOp Today!
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
Stay ahead of evolving threats with CyberSecOp’s managed security solutions.
Ransomware Recovery: How MSSPs Minimize Downtime and Data Loss
Ransomware attacks remain a top cybersecurity threat in 2025, capable of crippling businesses by encrypting critical data and demanding hefty ransoms. Recovery from these attacks is complex and costly, involving rapid incident response, reliable backups, and sometimes decryption solutions. Managed Security Service Providers (MSSPs) play a vital role in helping organizations minimize downtime and data loss through comprehensive ransomware recovery strategies. This article outlines how MSSPs provide expert incident response, implement robust backup strategies, and offer decryption solutions to effectively recover from ransomware incidents.
MSSP Incident Response: Fast, Coordinated Action to Contain and Recover
When ransomware strikes, every minute counts to limit damage and restore operations. MSSPs bring specialized expertise and 24/7 Security Operations Centers (SOCs) to provide:
Early Detection and Monitoring: Continuous monitoring detects ransomware activity early, often before encryption begins.
Rapid Containment: MSSPs isolate infected systems instantly to prevent lateral movement and further spread across the network.
Coordinated Response: Incident response teams execute well-established playbooks, coordinate communication with stakeholders, and oversee the entire containment and remediation process.
Forensic Analysis: Understanding attack vectors and compromised systems aids in complete remediation and strengthens defenses.
This fast, expert incident response drastically reduces downtime, preserves more data, and helps organizations regain control more quickly.
Backup Strategies: The Last Line of Defense
A strong, tested backup and recovery strategy is critical to mitigate the impact of ransomware:
Regular Automated Backups: MSSPs implement frequent, automated backups of critical data, ensuring recent restore points.
Immutable and Offline Backups: Storing backups in immutable or air-gapped environments prevents ransomware from encrypting or deleting backup data.
Geographically Distributed Backups: Duplicating backups across multiple locations protects against localized disruptions.
Backup Integrity Testing: Periodic verification of backup integrity ensures data can be reliably restored.
Rapid Recovery: MSSPs optimize recovery plans to restore business-critical systems and data with minimal downtime.
With robust backups, even if ransomware demands are not paid, organizations can restore operations without loss.
Decryption Solutions When Available
In some ransomware cases, MSSPs work with cybersecurity vendors and law enforcement to obtain and deploy decryption tools:
Vendor Partnerships: MSSPs have access to a database of known decryptors for specific ransomware variants.
Safe Deployment: MSSPs carefully test decryption tools within isolated environments to avoid further data damage.
Alternative Recovery: Decryption can speed up recovery when backups are unavailable or incomplete.
While not always possible due to evolving ransomware methods, MSSP expertise ensures decryption solutions are considered and applied safely when available.
Additional MSSP Ransomware Recovery Enhancements
Network Segmentation: Limits ransomware spread before it can impact the entire environment.
Vulnerability Management: MSSPs continuously identify and remediate vulnerabilities exploited by ransomware.
Employee Training: Awareness programs help prevent phishing and social engineering, common ransomware entry points.
Compliance and Reporting: MSSPs provide detailed reporting necessary for regulatory requirements post-incident.
Conclusion
Ransomware recovery is a multi-faceted challenge demanding expert coordination, proven backup strategies, and access to decryption resources. MSSPs like CyberSecOp minimize the costly downtime and data loss caused by ransomware by delivering proactive monitoring, rapid incident response, resilient backup solutions, and comprehensive recovery services tailored to today’s evolving threats.
Secure Your Business Against Ransomware with CyberSecOp
Protect your business with CyberSecOp’s expert managed security services designed for trusted ransomware defense and recovery.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
The Role of MSSPs in Cloud Access Security Broker (CASB) Implementation
As organizations increasingly migrate to cloud applications and services, securing data and users across these environments becomes a critical challenge. Cloud Access Security Brokers (CASBs) have emerged as essential security solutions, providing visibility, control, and threat protection for cloud usage. Managed Security Service Providers (MSSPs) play a pivotal role in implementing CASB solutions to help businesses secure their cloud applications effectively. This article explains how MSSPs deploy and manage CASB tools to enhance cloud security and compliance.
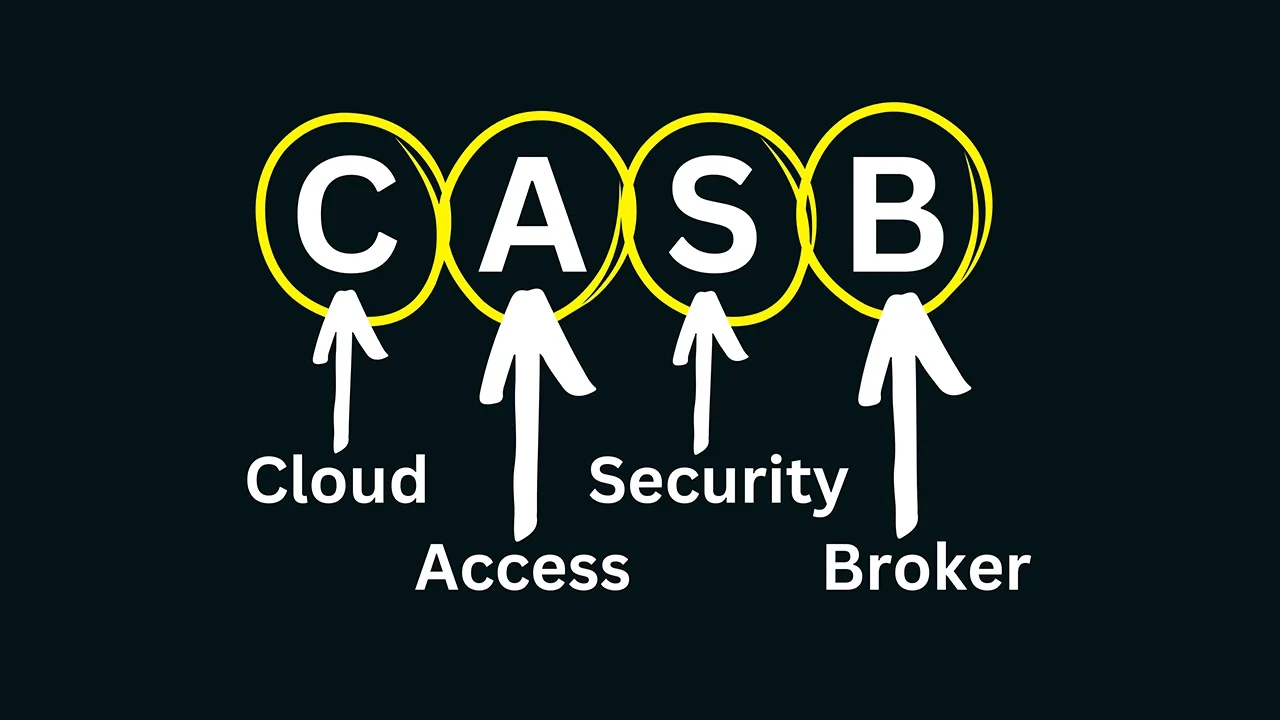
What is a Cloud Access Security Broker (CASB)?
A CASB acts as a security intermediary between users and cloud service providers. It enforces security policies across cloud applications, monitoring user activity and data flows to detect and prevent unauthorized access and data leakage. CASBs offer comprehensive capabilities, including:
Visibility into sanctioned and shadow cloud applications (Shadow IT)
Data Loss Prevention (DLP) to secure sensitive information
Threat protection through behavioral analytics and anomaly detection
Granular access control based on user, device, location, and risk context
Compliance enforcement with regulatory standards like GDPR, HIPAA, PCI-DSS
How MSSPs Help Businesses Implement CASB Solutions
1. Comprehensive Cloud Application Visibility and Risk Assessment
MSSPs deploy CASBs to provide organizations with a holistic view of their cloud usage, including unsanctioned applications that users might access without IT approval. This visibility helps assess risk levels and informs policy decisions to govern cloud access responsibly.
2. Tailored Policy Development and Enforcement
MSSPs work closely with businesses to develop customized access and usage policies enforced by CASBs. For example, MSSPs can restrict access to sensitive SaaS applications based on device compliance, user roles, geographic location, and network security posture, balancing security with user convenience.
3. Data Loss Prevention and Threat Mitigation
By leveraging built-in CASB DLP features, MSSPs help prevent sensitive data from being uploaded, shared externally, or exfiltrated. Real-time anomaly detection identifies suspicious activities like unusual download volumes, multiple login failures, or unauthorized data sharing attempts, enabling rapid mitigation.
4. Integration with Existing Security Architecture
MSSPs integrate CASB tools seamlessly with existing security infrastructure such as identity and access management (IAM), security information and event management (SIEM) systems, and endpoint protection platforms. This consolidation ensures more effective, coordinated cloud security controls.
5. Continuous Monitoring and Incident Response
With MSSP-managed CASB solutions, organizations benefit from continuous surveillance of cloud activity. MSSPs respond swiftly to alerts generated by CASBs to investigate potential breaches, suspicious user behavior, or compliance violations, reducing exposure and risk.
6. Simplified Regulatory Compliance
Compliance requirements for cloud data handling can be complex and vary by industry. MSSPs use CASB-generated audit trails, reports, and policy enforcement dashboards to help businesses meet regulatory mandates efficiently and confidently.
The Benefits of MSSP-Managed CASB Solutions
Expertise and Efficiency: MSSPs provide specialized knowledge and experience to configure and manage CASB deployments optimally.
Cost-Effective Security: SMBs and enterprises gain access to enterprise-grade cloud security without the burden of building in-house expertise.
Scalable Security: MSSPs manage and adjust CASB policies as organizations scale their cloud usage or adopt new applications.
Improved Security Posture: Proactive risk identification and mitigation reduce the likelihood of cloud data breaches.
Peace of Mind: Continuous monitoring and 24/7 support enable faster threat detection and response.
Conclusion
As cloud usage continues its rapid growth, securing cloud applications is paramount. CASBs offer powerful capabilities to enforce security and compliance policies across diverse cloud environments. Managed Security Service Providers (MSSPs) like CyberSecOp bring the expertise, tools, and ongoing management necessary to deploy and maintain effective CASB solutions tailored to business needs.
Partner with CyberSecOp to fortify your cloud security with MSSP-managed CASB services that provide full visibility, rigorous data protection, real-time threat detection, and compliance assurance.
Secure Your Cloud Applications with CyberSecOp
Contact us today to learn how CyberSecOp’s MSSP services featuring expert CASB implementation can safeguard your cloud environment:
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
CyberSecOp Ranked #1 on Gartner Peer Insights for Security Consulting Services Worldwide in 2025
CyberSecOp is proud to announce that we have achieved the prestigious distinction of being ranked Number 1 in Gartner Peer Insights for Security Consulting Services Worldwide in 2025. This top customer-rated recognition reflects our unwavering commitment to excellence, deep expertise, and outstanding customer experience in cybersecurity consulting and managed security services.
CyberSecOp is proud to announce that we have achieved the prestigious distinction of being ranked Number 1 in Gartner Peer Insights for Security Consulting Services Worldwide in 2025. This top customer-rated recognition reflects our unwavering commitment to excellence, deep expertise, and outstanding customer experience in cybersecurity consulting and managed security services.
What This Recognition Means for CyberSecOp and Our Clients
Being ranked number one among global security consulting service providers validates CyberSecOp’s holistic approach to cybersecurity. It highlights our ability to deliver actionable, effective solutions that empower organizations to meet evolving security challenges and regulatory requirements with confidence.
Our clients benefit from:
Trusted Expertise: Skilled teams that proactively guide organizations through complex regulations and cyber risks.
Innovative Solutions: Tailored security frameworks and best practices aligned with business goals.
Customer-Centric Service: Responsive support that acts as a true extension of client security teams.
What Our Clients Say
The foundation of this recognition is our clients’ satisfaction. Here are some of the most helpful reviews from Gartner Peer Insights:
"CyberSecOp provided an outstanding customer experience, consistently providing the right expertise at the right moments. Their team played a critical role in advancing our cybersecurity program and strengthening our policies during a pivotal time as we searched for a permanent CISO."
"Very good support from sales representative to the testing team."
"Structure and organization, content quality usability, language used is precise and professional."
"Overall, my experience with CyberSecOp has been excellent. From the initial contract negotiation through implementation and ongoing service, I have no complaints. SOC alerts would come in and be addressed in a timely manner. Staff was always friendly and helpful - they are more of an extension of your IT/Security team than a 3rd party MSSP."
Our Commitment to Excellence
CyberSecOp continuously invests in delivering industry-leading services combining strategic consulting, compliance expertise, and advanced technology implementations. This top rating encourages us to keep raising the bar to help organizations worldwide build resilient, compliant, and future-ready cybersecurity programs.
Partner with CyberSecOp, the #1 Ranked Security Consulting Service Provider
Discover how CyberSecOp’s award-winning team can elevate your cybersecurity posture and compliance readiness with tailored strategies and hands-on support.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
For more details and client testimonials, visit our Gartner Peer Insights page:
CyberSecOp on Gartner Peer Insights
Next-Gen SIEM: How MSSPs Are Redefining Security Operations for the Digital Age
In the rapidly evolving cybersecurity landscape of 2025, Managed Security Service Providers (MSSPs) are redefining security operations through the integration of Next-Generation Security Information and Event Management (SIEM) solutions. These modern SIEM platforms move far beyond traditional log collection and aggregation, offering real-time visibility, AI-driven threat detection, automated response, and deep integration across the entire security ecosystem. MSSPs leverage these advancements to enhance detection accuracy, reduce response times, and provide comprehensive protection to their clients.
What Makes Next-Gen SIEM Different?
Unlike legacy SIEMs that primarily focused on compliance reporting and manual log management, next-gen SIEMs deliver:
Cloud-Native Architectures: Designed for scalability and agility, supporting hybrid and multi-cloud environments.
AI and Machine Learning (ML): Automate anomaly detection, relentlessly reducing false positives by identifying patterns invisible to static rules.
Real-Time Correlation and Threat Intelligence: Seamlessly integrate data from endpoints, network devices, cloud workloads, identities, and external threat feeds.
Security Orchestration, Automation and Response (SOAR): Automate routine incident response workflows, accelerating containment without human delay.
User and Entity Behavior Analytics (UEBA): Establish baselines of normal behavior to detect insider threats and novel attack vectors.
Dynamic Attack Timelines: Automatically generate visual attack timelines, enabling rapid investigation by security analysts of all skill levels.
How MSSPs Leverage Next-Gen SIEM to Transform Security Operations
1. Unified and Contextualized Visibility
MSSPs deploy next-gen SIEM platforms that consolidate threat telemetry from diverse sources across on-premises, cloud, and endpoint environments. This holistic visibility enables the detection of stealthy, multi-vector attacks that often escape traditional tools.
2. AI-Driven Threat Detection and Prioritization
Machine learning models continuously analyze massive data volumes to identify anomalies and correlate seemingly unrelated events. AI-driven triage ranks alerts by severity, dramatically reducing alert fatigue and ensuring security teams focus on true threats.
3. Proactive Incident Response Automation
Next-gen SIEM integrated with SOAR capabilities empowers MSSPs to automate containment measures such as isolating compromised endpoints, blocking malicious IPs, or enforcing access controls—slashing mean time to respond (MTTR).
4. Predictive Security Analytics
By leveraging predictive models, MSSPs can anticipate threat actor behaviors and emerging attack patterns, enabling preventive actions before breaches occur. This predictive advantage is vital in defending against advanced threats like nation-state attacks and ransomware campaigns.
5. Compliance and Reporting Simplification
Automated compliance workflows, reporting, and audit trail generation ensure clients consistently meet regulatory standards while minimizing the administrative burden.
Leading Next-Gen SIEM Capabilities in MSSP Services
Several top next-gen SIEM platforms are reshaping security operations for MSSPs in 2025, including:
CrowdStrike Falcon Next-Gen SIEM: Known for integrated endpoint telemetry and real-time log analytics with reported 70% quicker detection times.
Microsoft Sentinel: Native integration with Azure and Microsoft 365 ecosystems, offering AI-powered automated threat hunting.
Splunk Enterprise Security: Renowned for scalability and customization for large enterprises.
Exabeam Fusion: Behavior-based analytics with automated attack timelines and response playbooks.
Gurucul: Combines SIEM, UEBA, and SOAR into a unified cloud-native platform with strong compliance management.
Hunters Security: AI-driven automation for alert investigation, tailored for mid-sized to large organizations.
Why MSSPs Using Next-Gen SIEM are Essential Partners
By integrating these sophisticated SIEM solutions, MSSPs help organizations:
Gain 360-Degree Security Visibility: Detect threats anywhere across increasingly complex hybrid environments.
Reduce Alert Fatigue: Employ AI-driven prioritization to focus efforts on high-risk threats.
Accelerate Response Times: Automate key incident response steps to contain threats rapidly.
Scale Security Operations Efficiently: Handle growing data volumes and clients without proportional staff increases.
Maintain Regulatory Compliance: Simplify audits with built-in compliance monitoring and reporting.
Conclusion
Next-Gen SIEM is redefining the capabilities and effectiveness of MSSPs in 2025 by delivering smarter, faster, and more integrated security operations. MSSPs harness these advanced platforms to provide customers with unparalleled threat detection, swift automated responses, reduced operational complexity, and enhanced compliance.
As cyber threats grow more sophisticated and attack surfaces expand, partnering with an MSSP leveraging next-gen SIEM technology—like CyberSecOp—becomes critical for organizations striving to strengthen their cybersecurity posture in the digital age.
Protect Your Organization with CyberSecOp's Next-Gen SIEM Powered MSSP Services
Ready to elevate your security operations with state-of-the-art SIEM solutions? Contact CyberSecOp today to learn how our managed security services leverage AI-driven next-gen SIEM to keep your business secure, compliant, and resilient.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
Phishing-as-a-Service: The New Cybercrime Business Model and How MSSPs Stop It
Phishing attacks continue to be one of the most pervasive and damaging cyber threats today, and in 2025, a new business model called Phishing-as-a-Service (PhaaS) is accelerating their spread. PhaaS democratizes phishing attacks, turning sophisticated cybercrime into a subscription-based service accessible even to individuals with little technical expertise. In this blog, we will expose the rise of PhaaS, explain why it poses such a serious threat to organizations, and describe how Managed Security Service Providers (MSSPs) like CyberSecOp implement advanced phishing defenses to protect businesses.
What is Phishing-as-a-Service (PhaaS)?
Phishing-as-a-Service is a cybercrime model where threat actors sell phishing tools, kits, hosting infrastructure, automation, and even customer support to criminals who want to conduct phishing campaigns. These services are often offered via subscription or one-time payments, primarily through underground channels like darknet forums or encrypted messaging platforms such as Telegram.
The PhaaS providers supply everything needed for a phishing attack, including:
Ready-made, convincing email templates mimicking well-known brands
Fake login websites that capture user credentials and bypass multi-factor authentication (MFA)
Tools to manage the stolen data and automate campaigns
Customer support to assist less experienced attackers in launching sophisticated scams
Because of this, even non-technical users can easily deploy large-scale phishing campaigns without building infrastructure or coding, which has led to a surge in phishing incidents globally.
Why is PhaaS a Growing and Dangerous Threat?
Lowering Barriers to Entry: PhaaS attracts a broad spectrum of attackers, from seasoned cybercriminals to novices, increasing the volume of phishing attacks rapidly.
Advanced Techniques: Many PhaaS kits now include capabilities like MFA token theft, adversary-in-the-middle (AiTM) attacks, and localized content to evade detection.
Wide Accessibility: Services are marketed openly on underground platforms, making phishing campaigns easier to launch than ever before.
High Success Rate: Even if just a small percentage of targets fall victim, the financial damage can be enormous due to stolen credentials, identity theft, and unauthorized access to critical systems.
In fact, Barracuda Networks reported that between 60% to 70% of all phishing attacks observed in early 2025 were delivered using the PhaaS model, with platforms like Tycoon 2FA dominating the attack landscape.
How MSSPs Protect Against PhaaS Attacks
Managed Security Service Providers like CyberSecOp play a crucial role in defending organizations from the escalating threat of Phishing-as-a-Service. Here’s how MSSPs implement advanced phishing defenses:
1. Continuous Email Threat Monitoring and Filtering
MSSPs deploy sophisticated email security gateways that use AI and machine learning to detect and block phishing emails before they reach end users. This includes scanning for malicious URLs, spoofed senders, and suspicious attachments.
2. Multi-Factor Authentication (MFA) Enhancements
While PhaaS often targets MFA mechanisms, MSSPs help businesses implement stronger MFA methods and adaptive authentication policies that reduce the success rate of phishing attempts exploiting stolen credentials or session cookies.
3. User Awareness and Phishing Simulation Training
Effective defense starts with informed users. MSSPs conduct regular phishing simulations and cybersecurity awareness training to educate employees on identifying phishing scams, reducing the chances of falling victim.
4. Threat Intelligence and Rapid Incident Response
MSSPs leverage global threat intelligence feeds to stay updated on emerging PhaaS kits, phishing campaigns, and attacker techniques. This intelligence enables rapid identification of compromise indicators and swift containment of attacks.
5. Advanced Endpoint and Network Monitoring
By monitoring endpoints and network traffic in real time, MSSPs can detect unusual login patterns, lateral movement, or data exfiltration attempts that might indicate successful phishing breaches.
6. Adversary-in-the-Middle (AiTM) Attack Mitigation
Specialized defenses focus on blocking AiTM-style phishing attacks that intercept MFA tokens and session data, employing advanced filtering and behavioral analytics.
Conclusion
Phishing-as-a-Service has transformed phishing from a technically demanding attack into a scalable, widespread cybercrime capable of bypassing traditional defenses. This new business model has led to a sharp increase in phishing attacks, posing critical risks to organizations of all sizes.
Partnering with an experienced MSSP like CyberSecOp is essential for navigating the challenges posed by PhaaS. Through a multi-layered defense strategy encompassing email security, user training, real-time monitoring, and threat intelligence, MSSPs protect businesses from falling victim to these evolving attacks.
Protect Your Organization Today
Stay one step ahead of phishing threats with CyberSecOp’s managed security services. Contact us to learn how our advanced anti-phishing solutions can defend your enterprise against Phishing-as-a-Service and other cyber threats.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
Why Small and Mid-Sized Businesses (SMBs) Are the New Prime Targets for Cyber Attacks
Small and mid-sized businesses (SMBs) are increasingly becoming prime targets for cyberattacks in 2025. This trend is driven by a combination of their growing digital footprint and perceived vulnerabilities compared to larger enterprises. Fortunately, Managed Security Service Providers (MSSPs) are stepping up to provide SMBs with enterprise-grade cybersecurity protection at a cost that aligns with their budgets.
Why Are SMBs Targeted More Frequently?
1. SMBs Represent a Large and Attractive Attack Surface
Nearly 43% of all cyberattacks target SMBs, a staggering proportion that underscores how threat actors view these organizations as lucrative and vulnerable targets. The increasing digitalization of SMB operations, including cloud adoption and remote work, expands their attack surface, making them more exposed.
2. Lower Cybersecurity Preparedness
Only about 14% of SMBs are adequately prepared to face cyberattacks. Many SMBs operate with outdated security technology or no cybersecurity solutions at all—20% report having no security technology. This lack of preparedness makes SMBs an easier target than well-defended large enterprises.
3. Human Error and Credential Theft
Human error accounts for over 95% of cybersecurity breaches in SMBs. Weak password practices, lack of multi-factor authentication (MFA), and insufficient employee training lead to vulnerabilities that cybercriminals exploit. Additionally, stolen credentials are responsible for around 30% of data breaches affecting SMBs, making them an outlet for cybercriminal activity.
4. Financial Impact and Disruption Potential
Despite being prime targets, SMBs often lack the financial resilience to recover from attacks. For example, 60% of SMBs struck by cyberattacks go out of business within six months. The average cost of a cybersecurity incident for SMBs varies widely but can be devastating, ranging up to hundreds of thousands of dollars. Phishing and ransomware attacks continue to be the leading threats, with ransomware hitting 82% of businesses under 1,000 employees.
5. Sophistication of Attacks on SMBs is Increasing
Cybercriminals are using advanced techniques, including AI-driven phishing and malware campaigns, making SMBs vulnerable to highly sophisticated attacks without the corresponding defense capabilities.
How MSSPs Provide Enterprise-Grade Protection at an Affordable Cost
1. Cost-Effective Access to Expert Cybersecurity Services
MSSPs give SMBs access to cybersecurity expertise and technologies that would otherwise be too costly or complex. Instead of hiring expensive in-house teams, SMBs can leverage MSSP resources for a predictable subscription fee, often lower than building and maintaining their own security operations.
2. 24/7 Monitoring and Incident Response
MSSPs provide continuous network and endpoint monitoring, allowing for real-time threat detection and faster incident response, minimizing damage and downtime. This constant vigilance helps SMBs respond immediately to threats they might otherwise miss.
3. Advanced Threat Detection Powered by AI and Automation
Using artificial intelligence and machine learning, MSSPs enhance threat detection accuracy and reduce false positives. This technology ensures SMBs can defend against modern, sophisticated attacks without dedicating extensive internal resources.
4. Comprehensive Security Solutions
MSSPs offer layered security solutions tailored to SMB needs, including:
Email and web filtering to combat phishing
Implementation and management of strong access controls like multi-factor authentication (MFA)
Regular vulnerability assessments and patch management
Endpoint protection and network security controls
5. Employee Training and Awareness
MSSPs educate SMB employees about cybersecurity best practices, particularly around phishing and social engineering, addressing the human factor that accounts for the majority of breaches.
6. Compliance and Risk Management Support
MSSPs help SMBs navigate increasingly complex regulatory environments by providing compliance monitoring and reporting, reducing the risk of costly fines.
Conclusion
Small and mid-sized businesses have become prime targets for cybercriminals due to their expanding digital footprint and often insufficient cybersecurity defenses. However, partnering with a Managed Security Service Provider (MSSP) offers SMBs access to enterprise-grade cybersecurity solutions tailored to their needs and budgets.
By leveraging MSSPs for continuous monitoring, advanced threat detection, employee training, and risk management, SMBs can significantly reduce their cyber risk, ensure business continuity, and safeguard their growth in an increasingly hostile cyber environment.
Protect Your SMB Today with CyberSecOp
Secure your business with CyberSecOp’s tailored MSSP solutions designed specifically for small and mid-sized businesses. Stay protected without breaking your budget.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
CyberSecOp Proudly Listed in CRN’s 2025 Managed Security 100
CyberSecOp is honored to be recognized in the prestigious 2025 CRN Managed Security 100 list, spotlighting the top Managed Security Service Providers (MSSPs) with expertise in cloud-based security services.
CyberSecOp is honored to be recognized in the prestigious 2025 CRN Managed Security 100 list, spotlighting the top Managed Security Service Providers (MSSPs) with expertise in cloud-based security services. This recognition underscores our commitment to delivering innovative, comprehensive cybersecurity solutions that empower businesses to safeguard their operations in an increasingly complex threat landscape.
The CRN MSP 500 list celebrates forward-thinking technology providers transforming the IT channel through managed services. The Managed Security 100 category specifically highlights MSPs excelling in cloud security, a critical area as organizations migrate workloads and data to hybrid and multi-cloud environments.
At CyberSecOp, we leverage advanced technologies, including AI-driven threat detection, continuous monitoring, and proactive incident response, to help clients stay ahead of emerging cyber threats while ensuring compliance with evolving regulations. Our inclusion in this elite group reflects our dedication to innovation, client success, and leadership in cybersecurity.
We thank CRN and The Channel Company for this recognition and remain committed to providing best-in-class managed security services that protect businesses today and into the future.
To learn more about CyberSecOp’s managed security services and how we can help your organization strengthen its cybersecurity posture, please contact us at:
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com
For more details on the CRN MSP 500 and the Managed Security 100 category, visit CRN’s official listing:
CRN 2025 MSP 500
CyberSecOp Recognized Among the Best Global Security Consulting Services by Gartner Peer Insights
CyberSecOp is proud to be featured in the 2025 Gartner Peer Insights review of top Security Consulting Services, Worldwide—a testament to our unwavering commitment to excellence in cybersecurity, compliance, and risk management.
CyberSecOp is proud to be featured in the 2025 Gartner Peer Insights review of top Security Consulting Services, Worldwide—a testament to our unwavering commitment to excellence in cybersecurity, compliance, and risk management.
What Sets CyberSecOp Apart?
Comprehensive Security Expertise
CyberSecOp stands out as a significant contributor in the field of information security, technology compliance, auditing, and regulatory matters. Our team brings deep expertise in designing and implementing information security-based internal controls that not only support future internal and external reviews but also ensure compliance with leading regulations and standards, including:
FFIEC (Federal Financial Institutions Examination Council)
GLBA (Gramm-Leach-Bliley Act)
NIST (National Institute of Standards and Technology)
SOC 3
PCI DSS (Payment Card Industry Data Security Standard)
HIPAA (Health Insurance Portability and Accountability Act)
HITRUST and more
Simplified Executive Reporting & Analytics
We simplify executive reporting and analytics related to information security risk management, empowering leadership teams to make informed decisions and maintain acceptable risk levels across the organization.
Holistic, Integrated Approach
CyberSecOp delivers a holistic approach to security, recognizing the interconnected nature of today’s business environments. Our integrated security frameworks are designed to:
Mitigate organizational threats across all business units
Provide actionable advice on technological risk and compliance
Align security strategies with business objectives for maximum resilience
Regulatory and Compliance Leadership
Our advisory services are tailored to help organizations navigate the complexities of regulatory compliance. We provide:
Expert guidance on regulatory requirements and best practices
Support in forming robust internal controls and policies
Ongoing monitoring and assessment to ensure sustained compliance
Why Choose CyberSecOp for Security Consulting?
Trusted by Boards and Executives: Our services are sought by boards of directors, CEOs, CROs, CISOs, CIOs, and IT leaders seeking to ensure their organizations maintain strong security postures and regulatory compliance.
Future-Ready Solutions: We anticipate emerging threats and regulatory changes, positioning our clients for long-term success.
Integrated Risk Management: Our frameworks and methodologies are designed to address the full spectrum of cyber risk, from assessment and policy development to incident response and recovery.
About Gartner Peer Insights Security Consulting Services
Gartner Peer Insights reviews and ranks the world’s leading security consulting providers, offering organizations a trusted resource for evaluating partners that can help them design, evaluate, and implement robust IT security strategies. CyberSecOp’s inclusion in this prestigious listing highlights our industry leadership and the value we deliver to clients worldwide.
Ready to Strengthen Your Security Posture?
CyberSecOp is dedicated to helping organizations achieve their security, compliance, and risk management goals. Whether you need to enhance your internal controls, prepare for regulatory audits, or build a resilient security framework, our team is here to help.
Contact us today to learn how CyberSecOp can elevate your organization’s cybersecurity and compliance strategy.
Customer Service: 1 866-973-2677
Sales: Sales@CyberSecOp.com