Zero Trust Services
Overview: Managed Security - MDR Services - Managed Compliance
CyberSecOp assists organizations that choose to migrate to a Zero Trust solution should fully embrace this security model and the mindset required for planning, resourcing, and operating under this security model in order to achieve the cybersecurity outcomes that a Zero Trust solution can deliver cybersecurity architects, integrators, and implementers in integrating disparate but related cybersecurity capabilities.
Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the hybrid workplace, and protects people, devices, apps, and data wherever they’re located.
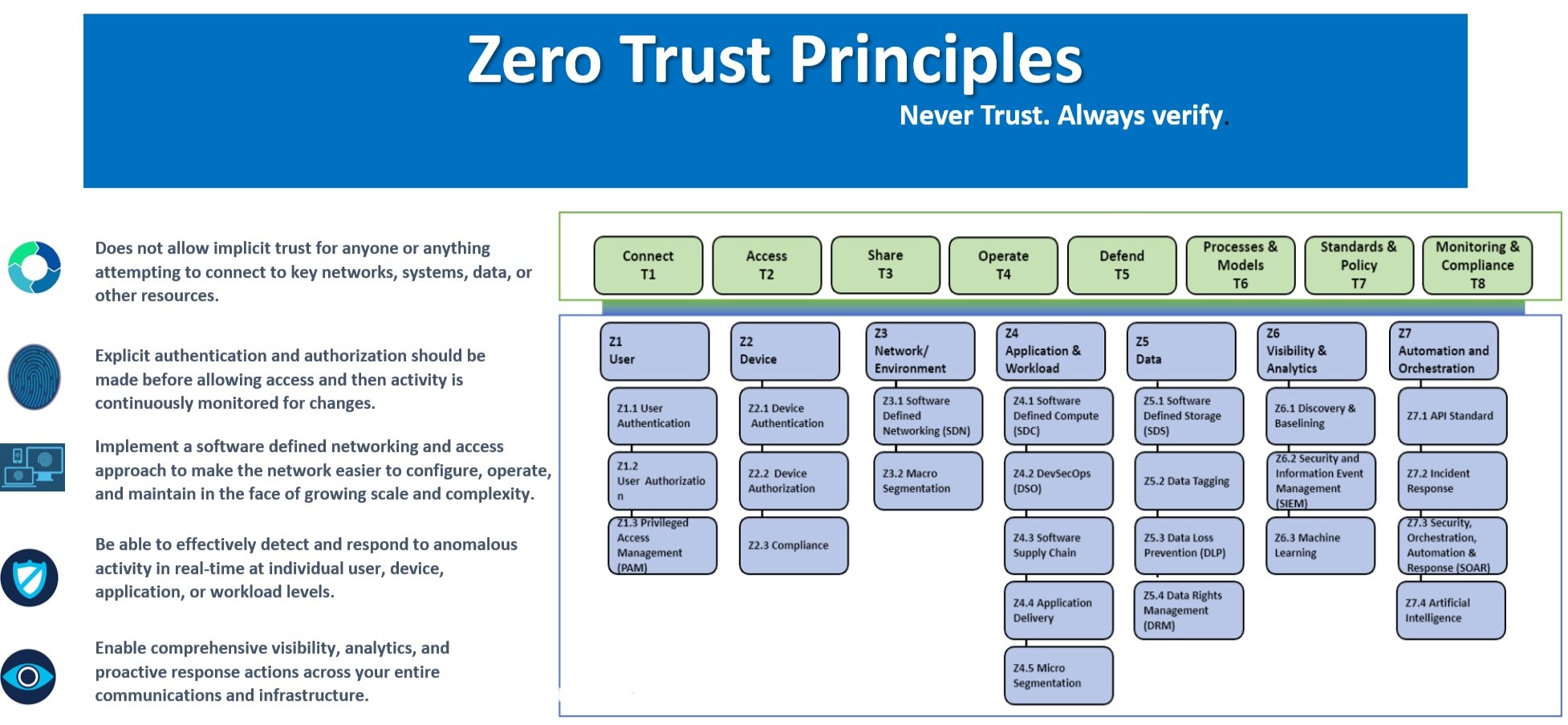
Embrace Zero Trust guiding principles
A Zero Trust solution requires operational capabilities that:
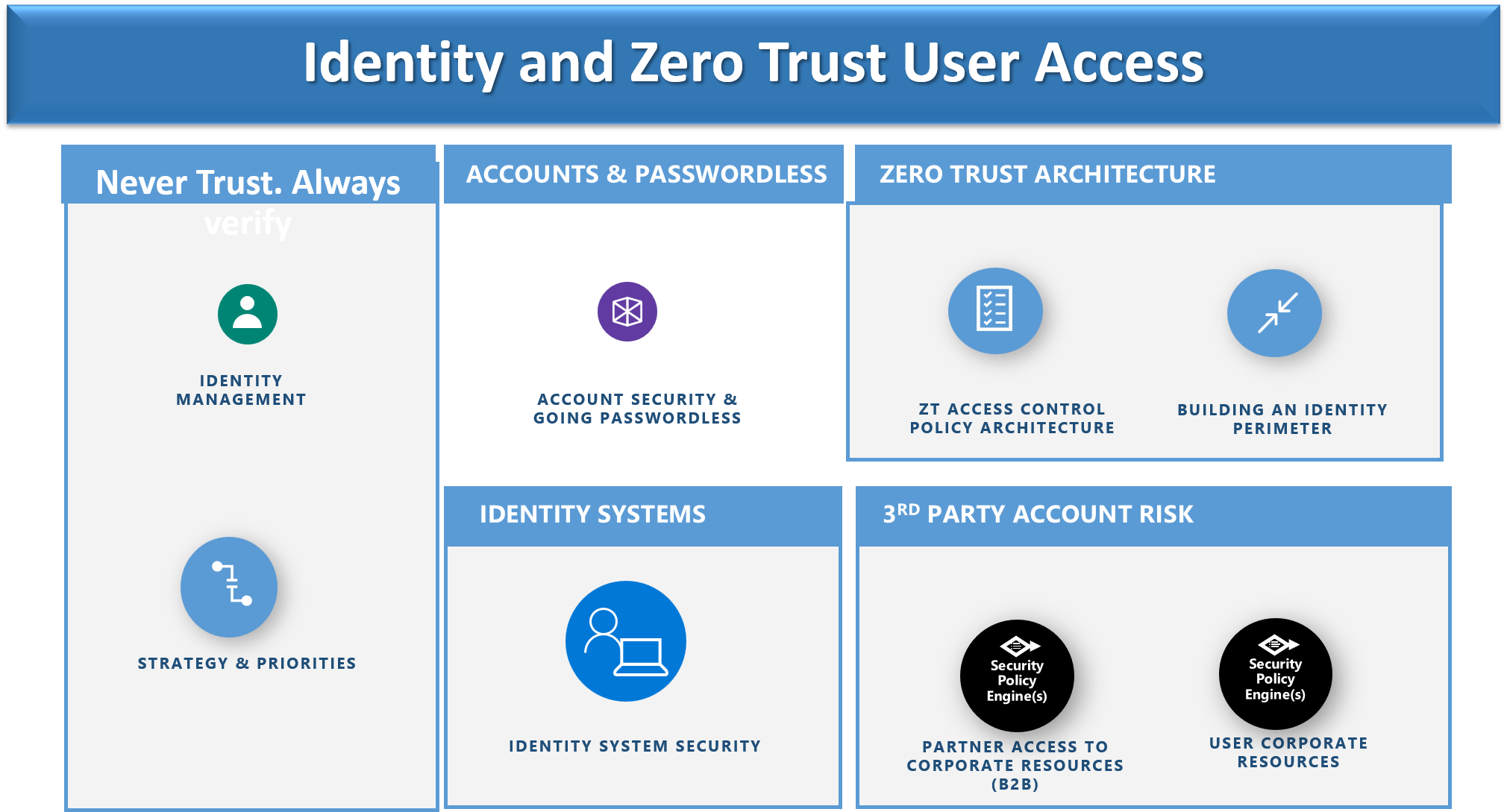
Never trust, always verify – Treat every user, device, application/workload, and data flow as untrusted. Authenticate and explicitly authorize each to the least privilege required using dynamic security policies.
Assume breach – Consciously operate and defend resources with the assumption that an adversary already has a presence within the environment. Deny by default and heavily scrutinize all users, devices, data flows, and requests for access. Log, inspect, and continuously monitor all configuration changes, resource accesses, and network traffic for suspicious activity.
Verify explicitly – Access to all resources should be conducted in a consistent and secure manner using multiple attributes (dynamic and static) to derive confidence levels for contextual access decisions to resources.
Leverage Zero Trust design concepts When designing a Zero Trust solution:
Define mission outcomes – Derive the Zero Trust architecture from organization-specific mission requirements that identify the critical Data/Assets/Applications/Services (DAAS).
Architect from the inside out – First, focus on protecting critical DAAS. Second, secure all paths to access them.
Determine who/what needs access to the DAAS to create access control policies – Create security policies and apply them consistently across all environments (LAN, WAN, endpoint, perimeter, mobile, etc.).
Inspect and log all traffic before acting – Establish full visibility of all activity across all layers from endpoints and the network to enable analytics that can detect suspicious activity,
CyberSecOp Zero Trust Security Framework Service
Implementing Zero Trust Security Posture
Zero Trust Cybersecurity Services
CyberSecOp Zero Trust Security services transforming businesses
CyberSecOp can transform your business into a Zero Trust model by focusing on the tools, policy, and procedures to protect these 5 pillars and substantially decrease the odds of a successful breach.
ZERO TRUST SECURITY SERVICES & Solutions
When all employees have the same access privileges, the network is vulnerable. VPNs may provide adequate security for on-prem resources, but only Zero Trust solutions offer the user-based access rules required for proper cloud security. Get started with our Zero Security Trust Solutions and Zero Trust Architecture consulting services.
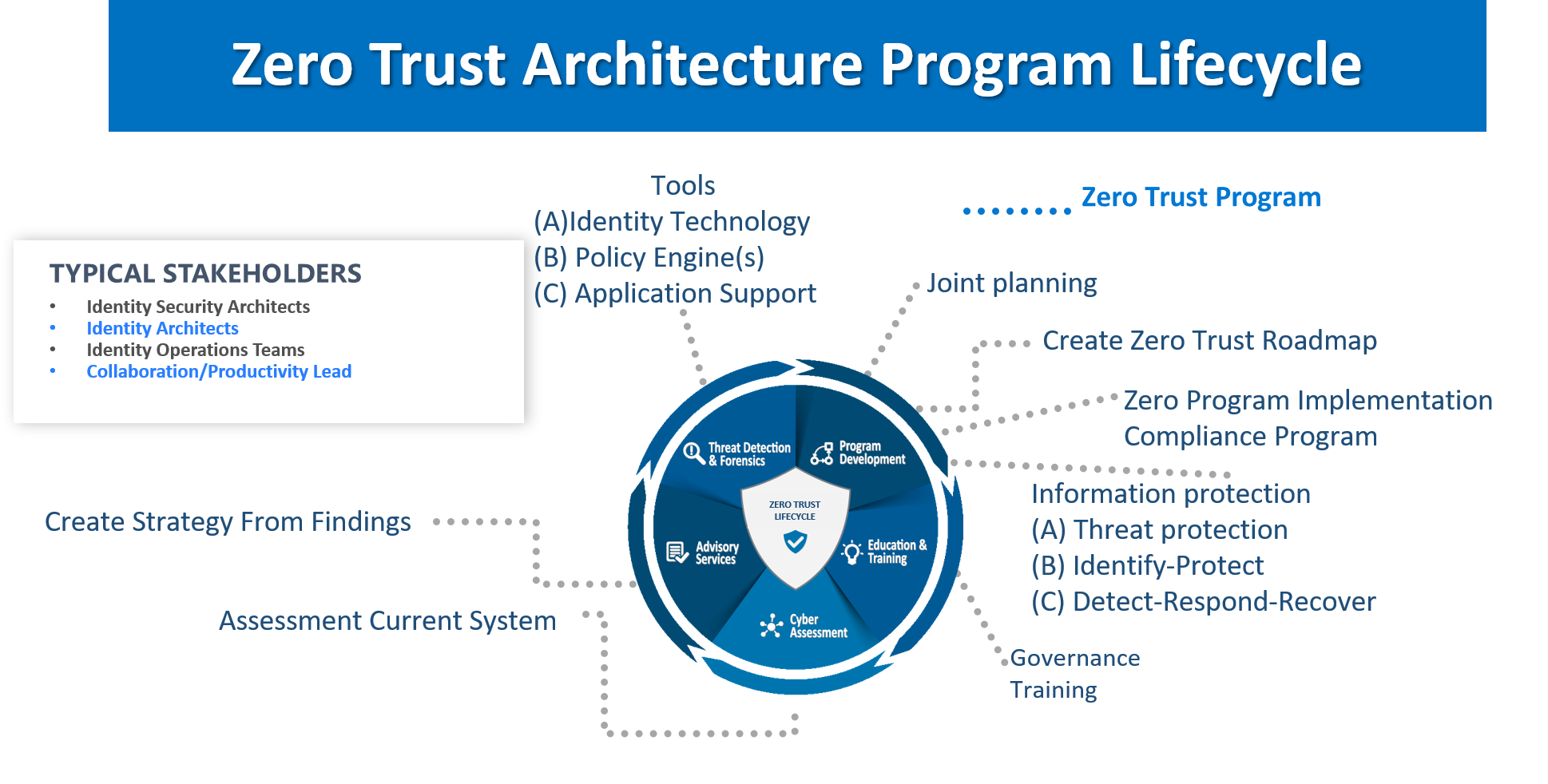
Zero Trust Architecture Program Services Lifecycle
ZERO TRUST MANAGED CYBER SECURITY Solutions
CyberSecOp is a Zero Trust Security Readiness Assessment service provider, offering a range of solutions related to the protection of computer systems within an organization. We cover computer security, and IT security. Cyber Security is a constantly evolving industry created in response to hacking, viruses, and other threats to personal and business data. CyberSecOp managed Zero Trust cybersecurity services will provide your business with expertise along the three stages of business cyber security protection services: assessment, security program implementation, and governance. We implement external and internal cyber security solutions with advanced IT security software and hardware solutions. CyberSecOp provides a number of Zero Trust cyber security tools to ensure end-to-end cybersecurity protection. We also provide IT outsourcing services that can address your company’s information technology needs.
Zero Trust End to End Cybersecurity Service
Zero Trust Cybersecurity services and strategic advisory consulting, incident response, design, and deployment services. we will implement a security program strategy to align information security policy, security controls, and strategy with business goals.
Zero Trust Security Readiness Assessment SERVICE PROVIDER
CyberSecOp is a leader in managed cyber security, and Zero Trust Security Readiness Assessment services. Our cyber security team will implement a secure framework and constantly monitor and protect your business from cyber threats. Our team of cyber security experts integrates business context intelligence, threat data, and cyber security insights to protect your assets and data. The risk scene develops with rising rates, it takes more oversight with cyber security services to effectively ensure your organization is secure from cyber threats. Our team will work with your firm to identify any risks or threats it may face. We will deliver recommendations that highlight security flaws in your environment, and the steps needed to remediate these issues.
Zero trust CYBERSECURITY AS A SERVICE (ZTCSAAS)
Proactive Zero Trust Cyber Security as a Service (ZTCSaaS) to mitigate cyber risks, every business needs a defense in depth which include IT security solutions and cybersecurity experts who can deploy and monitor them.
Transform your cybersecurity, strengthen it and become proactive, effective, and resilient. Cybersecurity is a core business requirement, providing a secure foundation to transform your enterprise and support your business. Ready to see how CyberSecOp Cyber Security and Zero Trust Security Readiness Assessment Services can help?