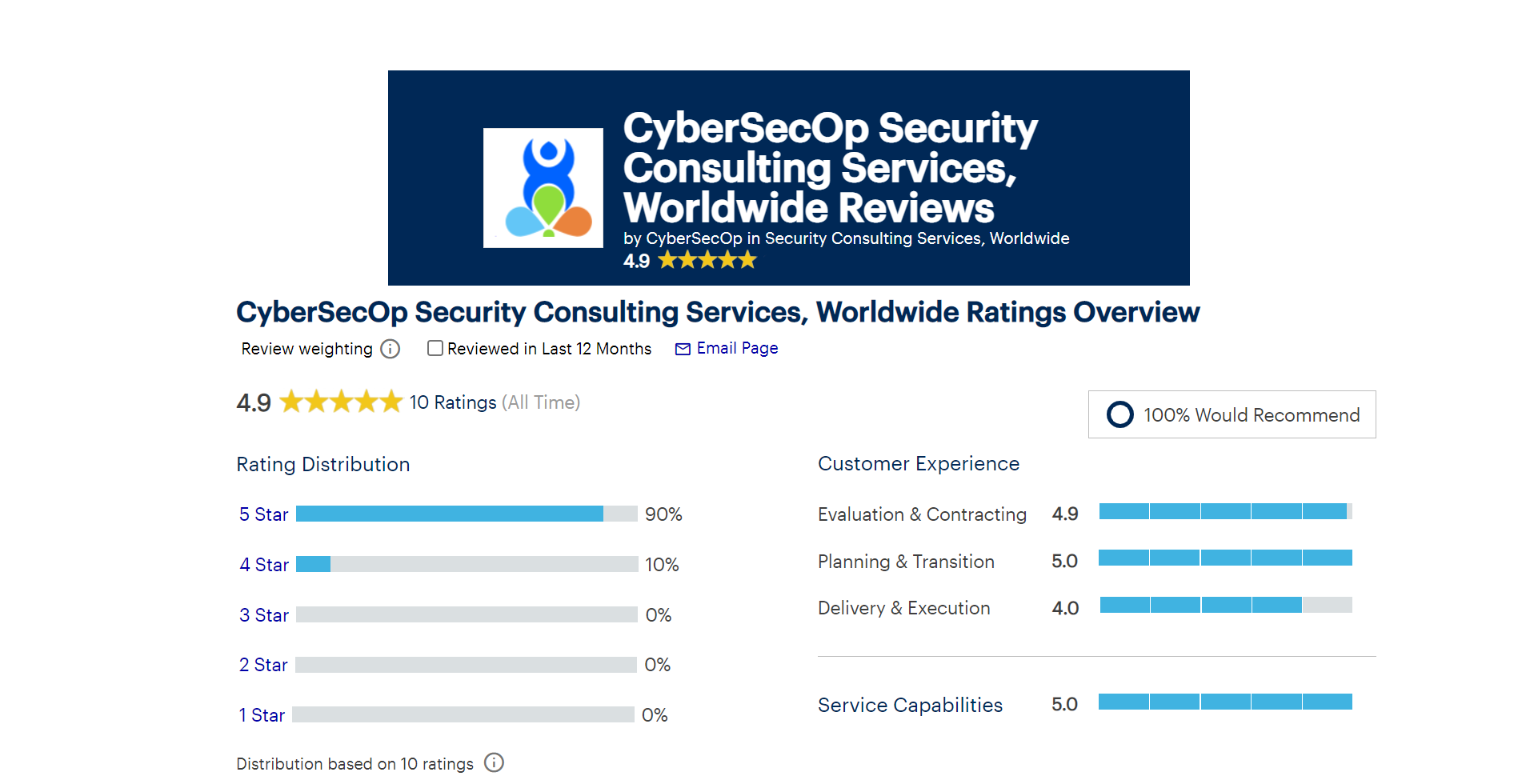
Zero Trust focuses on 5 pillars
1. Device Trust
2. User Trust
3. Transport and Session Trust
4. Application Trust
5. Data Trust
CyberSecOp can transform your business into a Zero Trust model by focusing on the tools, policy, and procedures to protect these five pillars and substantially decrease the odds of a successful breach.
ZERO TRUST SERVICES & ZERO TRUST PLATFORM
With Zero Trust network access for your private apps and systems, you no longer have to choose between user experience and security. CyberSecOp Managed Zero Trust services were built with a new approach that directly creates zero trust connections between the users and the applications to solve this unique challenge. As a scalable, cloud-native platform, it enables digital transformation by securely connecting users, devices, and applications anywhere without relying on network-wide access. This platform is delivered by five key architecture attributes unique to the CyberSecOp Managed Zero Trust services. Together, they enable organizations to provide strong security and a great user experience to their employees and customers.
When all employees have the same access privileges, the network is vulnerable. VPNs may provide adequate security for on-premise resources, but only Zero Trust solutions offer the user-based access rules required for proper cloud security.
Our Zero Trust solutions and services utilize multi-layered cybersecurity protection to transform your business with cybersecurity orchestration, automation, cybersecurity consulting, cloud, and managed security services. We implement a comprehensive approach to secure and protect businesses from cyber threats. Our cybersecurity services cover all the following areas needed for a zero-trust secure environment: Cybersecurity Program Strategy, Risk Management, Risk Assessment, Threat Intelligence, Incident Response, Advanced Malware & Ransomware Protection, Perimeter Security, Application Assessment, & Security Monitoring Services. We know where you are and how to protect your organization with a cybersecurity gap analysis to identify a more precise road map and a more robust cybersecurity program.
Zero trust networks, of course, extend beyond security. They are also inherently agile, a vital benefit for an increasingly remote workforce. As massive remote crews put unprecedented strain on cloud resources, the more stability and resilience you can build into your architecture, the better. Rather than backhauling remote data to a static data center, zero trust applications connect directly into your network from outside the perimeter, which helps free up bandwidth for DevOps and access business-critical cloud services.
ADOPT OUR ZERO TRUST SECURITY MODEL DEFENSE APPROACH
AUTOMATED PKI LIFECYCLE MANAGEMENT ZERO TRUST
The automated PKI lifecycle management platform enables Zero Trust by utilizing Public Key Infrastructure (PKI) certificates and key pairs, strengthening digital identities, and securing the connections between entities beyond the firewalled network architecture. In this age of digital transformation, the Zero Trust model increases the need for a consolidated, automated, and modern approach to PKI.
SECURE INTERNET GATEWAY
Control desktop, laptop, and mobile device access to malicious and inappropriate websites.
SECURE WEB GATEWAY
Protect against every kind of threat and ensure strict compliance with policies without slowing down your users.
ANTI SPAM & EMAIL GATEWAY
Secure Email Gateway protects organizations and employees from spear-phishing, malware, spam, and zero-day attacks. To ensure zero trust by removing spam and malicious email traffic before it enters your network to ensure zero trust.
ADVANCED ENDPOINT PROTECTION
Secure all your servers, desktops, laptops, and mobile devices from known and unknown malware–without requiring signatures or updates.
WEB APPLICATION FIREWALL
Powerful, real-time edge protection for
web apps and websites providing advanced
filtering, security, and intrusion protection.
SIMPLIFY COMPLIANCE REPORTING
Meet compliance requirements with no extra work. CyberSecOp Consultants have you covered, delivering streamlined reports of system access across the organization and zero trust technologies.
CYBER SECURITY OPERATIONS CENTER
Your always-on certified cybersecurity professionals team provides 24/7/365 surveillance and remediation services to ensure zero trust.
DATA LOSS PREVENTION
Monitor and control the movement of sensitive and confidential data across the network. Implement a ‘zero-trust’ data loss prevention (DLP) strategy utilizing activity, system-access, schedule, and content-based rules to ensure zero trust.
SINGLE SIGN-ON
A secure cloud single sign-on solution that IT, security, and users will love. Single sign-on solutions can quickly connect to and sync from identity stores including AD, LDAP, HR systems, and other third-party identity providers to ensure zero trust.
MULTI-FACTOR AUTHENTICATION
Secure, intelligent access to delight your workforce and customers. Secure your accounts and apps with a robust multi-factor authentication solution to keep the right people in and the wrong people out. Protect all your resources, including customer-facing and enterprise apps that store your most sensitive data to ensure zero trust.
SECURITY INCIDENT EVENT MANAGEMENT
We are providing actionable intelligence leveraging current events and data. Our SIEM collects logs and circumstances of the network traffic and web assets, security devices, operating systems, applications, and databases and reviews the vulnerabilities using artificial intelligence to process to ensure zero trust.
REMOTE MONITORING AND MANAGEMENT
Remote Monitoring and Management (RMM) is remote monitoring software that allows you to remotely monitor and manage endpoints, computers, mobile devices, and networks from a centralized console to ensure zero trust.
MANAGED CYBERSECURITY SERVICES
CyberSecOp is a cybersecurity service provider offering a range of solutions related to protecting computer systems within an organization. Cybersecurity is a constantly evolving industry created in response to hacking, viruses, and other personal and business data threats. CyberSecOp-managed cybersecurity services will provide your business with expertise in the three stages of business cybersecurity protection services: assessment, security program implementation, and governance. We implement external and internal cybersecurity solutions with advanced IT security software and hardware solutions. CyberSecOp provides several cybersecurity tools to ensure end-to-end cybersecurity protection. We also offer IT outsourcing services to address your company’s information technology needs.
End to End Cybersecurity Services
We offer cybersecurity and strategic advisory consulting, incident response, design, and deployment services. We will implement a security program strategy to align information security policy, security controls, and plan with business goals.
LEADING MANAGED CYBERSECURITY SERVICE PROVIDER
CyberSecOp is a leader in managed cybersecurity services. Our cybersecurity team will implement a secure framework and constantly monitor and protect your business from cyber threats. Our cybersecurity experts integrate business context intelligence, threat data, and cybersecurity insights to protect your assets and data. The risk scene develops with rising rates; it takes more oversight with cybersecurity services to effectively ensure your organization is secure from cyber threats. Our team will work with your firm to identify any risks or threats it may face. We will deliver recommendations highlighting security flaws in your environment and the immediate steps to these issues.
CyberSecOp offers proactive Cybersecurity as a Service (CSaaS) to mitigate cyber risk. Every business needs defense in-depth, includincludessecurity solutions and cybersecurity experts who can deploy and monitor them.
Transform and strengthen your cybersecurity to become proactive, effective and resilient. Cybersecurity is a core business requirement, providing a secure foundation to transform your enterprise and support your business. Ready to see how CyberSecOp Cybersecurity Services can help?