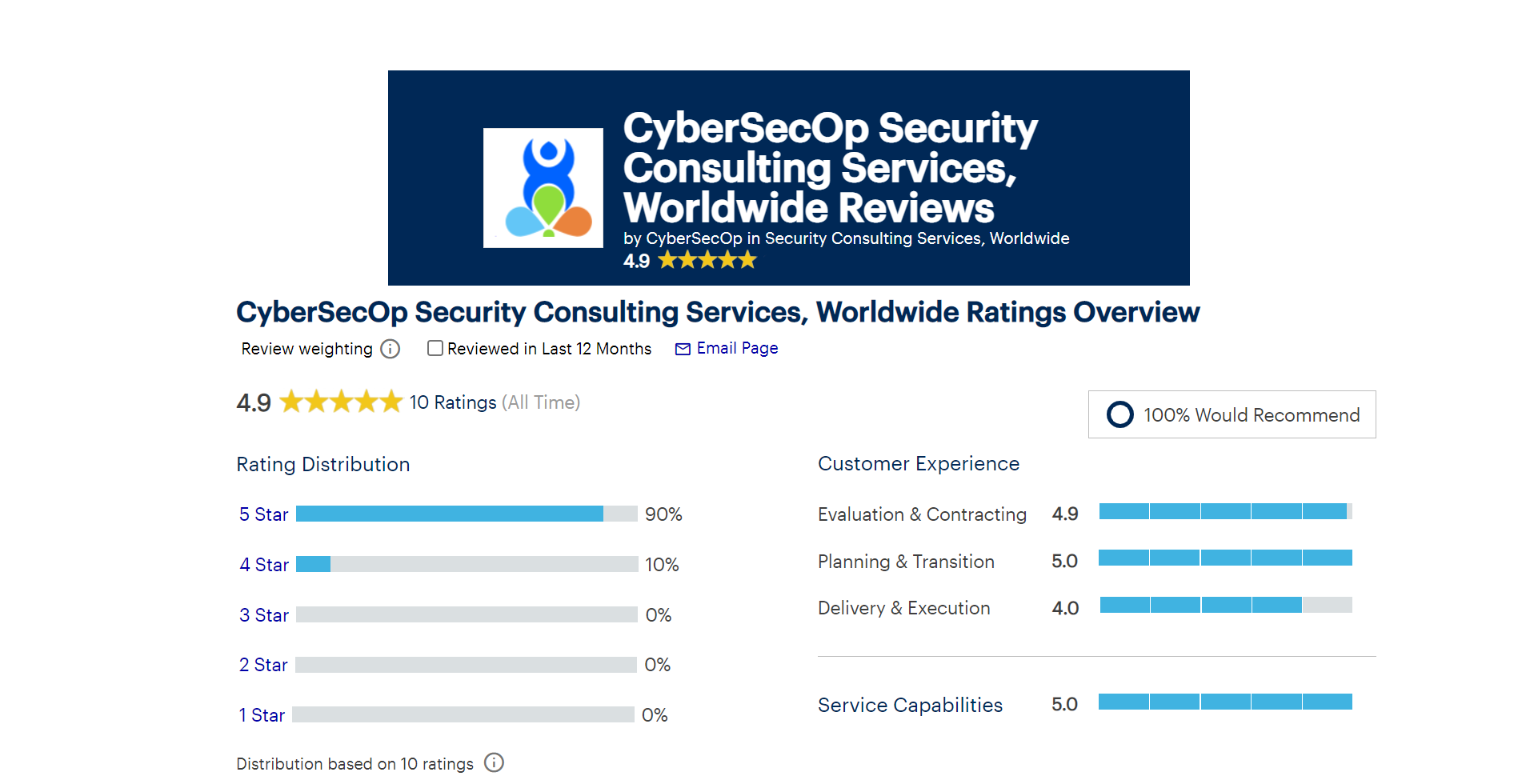
CyberSecOp receives the highest overall score on Gartner Peer Insights for Security Consulting Services, Worldwide in 2022.
June 8, 2022 - CyberSecOp today announced that its Security Consulting Services received a 4.9 out of 5 overall rating from Gartner Peer Insights, placing CyberSecOp in the top two on Gartner’s Security Consulting Services Worldwide category.
"Peer reviews are extremely valuable for evaluating any purchase decision," said Josh Bauer, Executive Director at Loxo Oncology/Lilly. “CyberSecOp appears to actively and continuously listen to us as a customer to ensure they deliver innovative solutions and a valuable user experience."
“CyberSecOp is honored to receive our current ranking status and client feedback, and we will continue to prioritize customer satisfaction across the board." Vincent LaRocca, CEO & Co-Founder.
2022 Gartner Peer Insight
Gartner Peer Insights is the firm's platform for rating and reviewing enterprise technology solutions by end-user professionals for end-user professionals. Through user-contributed reviews from people who have actually used the services, the rating system combines expert opinions and peer insights. Peer Insights User Reviews offers a suite of interactive features for technology buyers, including the ability to customize evaluation criteria to create a quadrant view tailored to the user's goals and priorities. The platform employs rigorous methodologies, processes, and quality standards to deliver unbiased research and authentic peer reviews.
What is Gartner’s research?
Gartner research: Trusted insight for executives and their teams
Gartner research, which includes in-depth proprietary studies, peer and industry best practices, trend analysis, and quantitative modeling, enables us to offer innovative approaches that can help you drive stronger, more sustainable business performance.
Gartner research is unique, thanks to:
Independence and objectivity
Our independence as a research firm enables our experts to provide unbiased advice you can trust.
Actionable insights
Gartner’s research is unbiased, containing vital takeaways and recommendations for impactful next steps.
Proprietary methodologies
Our research practices and procedures distill large volumes of data into clear, precise recommendations.